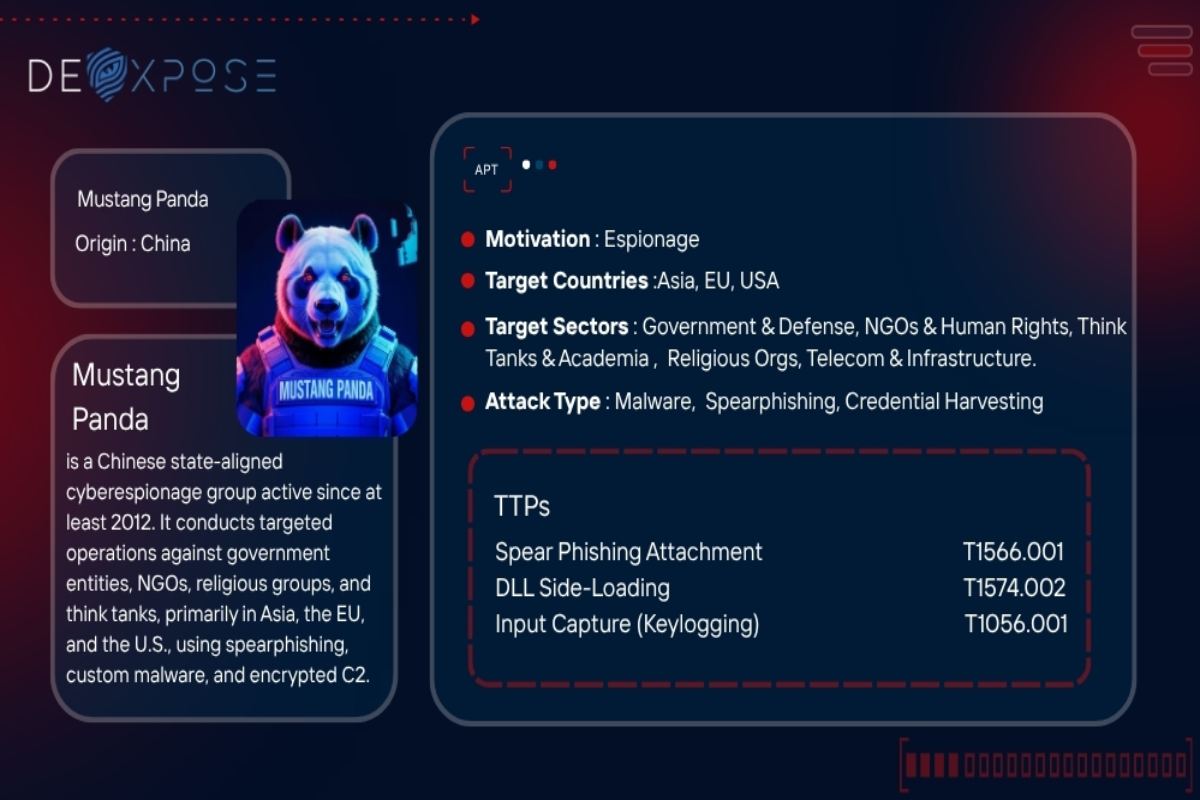
Mustang Panda is a highly persistent and adaptive Chinese state-linked cyber espionage group operational since at least 2012. Known by multiple aliases—including Red Delta, TA416, and Stately Taurus—this threat actor has consistently targeted entities of strategic relevance to the People’s Republic of China (PRC), using a sophisticated blend of spear-phishing, custom malware, and stealthy command-and-control (C2) operations.
Their focus is not on headline-grabbing zero-day vulnerabilities but on adequate tradecraft: finely tuned phishing lures, malicious payload obfuscation, and geopolitical targeting. Mustang Panda’s targets typically include government agencies, non-governmental organizations (NGOs), think tanks, religious institutions, and civil society organizations across Asia, Europe, Africa, and North America.
In this in-depth profile, we’ll examine Mustang Panda’s evolving tactics, malware arsenal, notable campaigns, and strategic objectives, providing a clear view of one of the world’s most active and effective cyber espionage groups.
Strategic Targeting: Who Does Mustang Panda Attack?
Mustang Panda aligns its campaigns closely with the Chinese government’s geopolitical goals. Its operations span continents but are laser-focused on collecting intelligence that supports Beijing’s strategic interests.
Primary target regions include:
- Southeast Asia
- European Union nations
- The United States and allies
- Countries with Tibetan or Uyghur diaspora
- Regions with ongoing political friction involving China
Target sectors and organizations:
- Ministries of Foreign Affairs, Defense, and Interior
- Diplomatic missions and intelligence agencies
- Religious institutions (mainly Catholic and Tibetan)
- NGOs focused on human rights and democracy
- Think tanks and policy research groups
- Telecom, energy, and transportation infrastructure
- Universities and research institutions
- Aviation and logistics providers
Notable targeted countries include Australia, Bangladesh, Belgium, Cambodia, the Czech Republic, Ethiopia, France, Germany, India, Indonesia, Japan, Mongolia, Myanmar, Nepal, Pakistan, Philippines, Russia, South Korea, Sweden, Taiwan, Thailand, the UK, the USA, and Vietnam.
 Summary image of Mustang Panda’s attack patterns.
Summary image of Mustang Panda’s attack patterns.
Operational Tactics and Attack Techniques
Mustang Panda’s operations stand out not through groundbreaking malware but through consistency, discipline, and a clear understanding of their targets. Here’s how they typically operate:
1. Initial Access via Spear Phishing
The group typically delivers malicious payloads through spear-phishing emails containing ZIP, RAR, or LNK files [T1566.001]. Lures are often politically themed to increase credibility, centered on events in Tibet, diplomatic communiqués, or regional summits.
2. USB-Based Propagation
Mustang Panda uses removable media to spread malware in highly secured or air-gapped environments. The HIUPAN worm (USB worm) facilitates lateral movement via infected flash drives [T1091].
3. DLL Sideloading and In-Memory Execution
DLL sideloading [T1574.002] is their core execution strategy. Legitimate signed binaries sideload malware loaders like Claimloader or ToneShell, inject second-stage payloads directly into memory [T1055.001], bypassing many antivirus solutions.
4. Persistence & Privilege Escalation
Persistence is maintained through:
- Scheduled tasks [T1053.005]
- Service registration [T1569.002]
- Custom-built tools like SplatCloak, which evade endpoint detection and response (EDR) tools at the kernel level
Privilege escalation often relies on token impersonation [T1134.002], especially in environments where lateral movement is key to the mission.
5. Lateral Movement & Internal Routing
Mustang Panda uses internal proxy tools like StarProxy [T1090.001] to move laterally and maintain internal routing, enabling stealthy, encrypted communication within segmented networks.
6. Data Exfiltration & Evasion
Collected data—often via keyloggers or clipboard monitors (PAKLOG, CorKLOG)—is exfiltrated using encrypted channels like FakeTLS or tunneled protocols. Payloads are usually encrypted with XOR or RC4 [T1573.001], and C2 traffic is disguised via protocol impersonation [T1001.003].
 Key insights into Mustang Panda’s threat activity.
Key insights into Mustang Panda’s threat activity.
Mustang Panda Malware Arsenal
The group’s toolset is diverse, modular, and tailored for stealth and flexibility. Here are the most prominent malware families and utilities associated with Mustang Panda:
Claimloader / Pubload / Pubshell
A three-stage infection chain involving:
- Claimloader (sideloaded DLL)
- Pubload (downloads payloads)
- Pbshell (reverse shell)
ToneShell
A versatile backdoor used in high-profile campaigns. Features include encrypted communication (FakeTLS), payload execution, DLL injection, and fileless persistence.
StarProxy
Used for tunneling C2 traffic between hosts, enabling Mustang Panda to bypass perimeter security.
SplatCloak
A custom kernel-mode driver that disables Windows Defender and Kaspersky callbacks. Delivered via SplatDropper.
PAKLOG / CorKLOG
Keyloggers that record keystrokes and clipboard data. CorKLOG encrypts logs with a unique 48-character RC4 key.
MQsTTang
A lightweight backdoor using the MQTT protocol—standard in IoT environments—for C2 communication.
PlugX
A modular RAT used across multiple Chinese APT groups and notably deployed during attacks on Vatican institutions and U.S. defense networks.
USB Worm (HIUPAN)
Designed for spreading across air-gapped environments using infected USB drives.
FDMTP / PTSOCKET
Used to locate, compress, and exfiltrate sensitive documents (PDFs, PPTs, DOCs) to attacker-controlled servers.
Exploited Vulnerabilities
Mustang Panda frequently integrates public vulnerabilities into their delivery chain, especially to enhance privilege escalation or remote code execution.
- CVE‑2017‑0199 – Exploits Microsoft Office RTF files for RCE
- CVE‑2021‑1675 / CVE‑2021‑34527 (PrintNightmare) – Enables remote code execution via Windows Print Spooler
- CVE‑2021‑40444 – MSHTML flaw allowing ActiveX control abuse in Office documents
Real-World Campaigns and Case Studies
1. 2025 – Targeting the Tibetan Community
Spear-phishing emails themed around the Dalai Lama’s 90th birthday and the World Parliamentarians’ Convention on Tibet were used to infect activists and policy workers.
Payload: Claimloader → Pubload → Pubshell C2: Encrypted channel using FakeTLS
2. 2025 – Myanmar Campaigns with Enhanced Tooling
ToneShell, StarProxy, and keyloggers (PAKLOG, CorKLOG) were deployed in Myanmar-based NGOs and governmental bodies. SplatCloak was used to bypass EDR solutions.
3. 2024 – USB Worm Campaign in APAC
HIUPAN worm enabled stealthy propagation in countries like Vietnam, Cambodia, and the Philippines. Post-infection, attackers deployed PUBLOAD and PlugX for persistence.
4. 2021–2023 – Southeast Asian Government Infiltration
Mustang Panda (under the alias Stately Taurus) breached a Southeast Asian government. They maintained long-term access using ToneShell and ShadowPad, exfiltrating sensitive documents and credentials.
5. 2020 – RedDelta Campaign Targeting the Vatican
Using Catholic-themed lures, Mustang Panda infected diplomatic and religious personnel in Hong Kong and the Vatican using PlugX and DLL sideloading techniques.
Also Read: Akira Ransomware Attack on SIB-Tryck Holding Explained
Techniques for Evasion and Obfuscation
Mustang Panda is known for its highly advanced anti-detection measures:
- Encrypted Payloads: XOR, RC4, and custom encoding schemes
- Protocol Impersonation: Mimics legitimate traffic to blend in
- Kernel-Level EDR Bypass: SplatCloak turns off Defender and Kaspersky hooks
- Obfuscation Techniques: Control flow flattening, mixed boolean logic, and DJB2-based API hashing
- Self-Deletion: Malware cleans up after execution to minimize forensic artifacts
Why Mustang Panda Remains a Persistent Threat
Mustang Panda focuses on the long term, unlike many financially motivated cybercriminal groups. Their intelligence-driven campaigns often align with diplomatic summits, political anniversaries, or contentious legislation. Their adaptability—from USB worms to advanced backdoors—demonstrates operational maturity and state support.
They are not just a technical threat but a geopolitical actor in cyberspace. Understanding their methods is crucial for defenders across sectors.
Final Thoughts
Security teams must adopt a defense-in-depth approach to counter Mustang Panda:
- Email Filtering: Detect phishing attempts using ZIP/RAR/LNK payloads
- Behavioral Analysis: Identify unusual DLL sideloading or task creation
- Endpoint Hardening: Block unsigned kernel-mode drivers and audit driver installation events
- Network Monitoring: Look for FakeTLS and protocol anomalies
- Threat Intelligence: Track Mustang Panda’s evolving TTPs to anticipate new campaigns
Mustang Panda represents the modern face of cyber-espionage—strategic, stealthy, and deeply rooted in geopolitical motives. As their capabilities evolve, so must the world’s collective defense.
Frequently Asked Questions
Who is Mustang Panda, and what motivates their cyber operations?
Mustang Panda is a Chinese state-linked cyber espionage group that targets organizations aligned with China’s geopolitical and ideological interests. Their campaigns are driven by strategic intelligence gathering, especially in Southeast Asia, Europe, and regions with sensitive political relevance. The group prioritizes long-term access and stealth over flashy, destructive attacks.
How does Mustang Panda typically gain initial access to target systems?
They primarily use spear-phishing emails with malicious ZIP, RAR, or LNK attachments that appear politically or socially relevant to the victim. These lures often exploit public vulnerabilities in Microsoft Office and Windows systems. Once opened, the payload initiates multi-stage malware delivery for covert access.
What types of organizations are most at risk from Mustang Panda attacks?
Government agencies, NGOs, think tanks, religious institutions, and sectors like telecom, aviation, and energy are frequently targeted. These targets often hold policy influence or sensitive data valuable to China’s national interests. Mustang Panda’s targeting is always intentional, not random.
What kind of malware does Mustang Panda use in their operations?
Their arsenal includes custom malware like ToneShell, Claimloader, StarProxy, and SplatCloak, among others. These tools are designed for stealth, persistence, and lateral movement within secure networks. Many use DLL sideloading and encrypted C2 channels to avoid detection.
How can organizations defend against Mustang Panda’s techniques?
Defense begins with employee awareness and advanced phishing detection systems to block spear-phishing attempts. Organizations should also enforce patch management and EDR solutions and monitor for unusual remote access or DLL sideloading behaviors. Layered security and threat hunting are essential to detect their covert activities.