Dark Web monitoring
Gain Comprehensive Visibility Into Your Organization's Exposure On The Dark Web.
Breaches monitoring
Stay Ahead Of The Curve With Our Continuous Monitoring Service For Latest Breach Services.
Attack surface mapping
Our Attack Surface Mapping Service Offers A Full Overview Of Your Exposed Assets.
Monitoring
Darkweb
In a world that is increasingly interconnected and reliant on digital infrastructure, the urgency of easing cybersecurity threats, vigilantly staying ahead of potential breaches
DeXpose offers a cutting-edge solution to monitor the dark web for any signs of compromised credentials, providing an extra layer of security to safeguard your sensitive information.

Understanding The Dark Web:
The dark web, a hidden corner of the internet, is notorious for harboring illegal activities and hosting markets where stolen data, including compromised credentials, is bought and sold. DeXpose's advanced monitoring system scans the dark web's unindexed corners to identify if your organization's credentials are being traded.
Why Should Your Organization Care?
Cybercriminals often capitalize on reused credentials from breaches to infiltrate various online accounts. By monitoring the dark web, DeXpose helps you proactively detect compromised credentials associated with your domain, preventing unauthorized access before it happens.
Data Collection
DeXpose's web crawling technology collects data from various sources across the dark web, including underground forums and marketplaces.
Data Analysis
Our advanced algorithms analyze the collected data to identify any references to your organization's domain and associated credentials.
Notification
Alert Generation
When compromised credentials are detected, the system generates real-time alerts, notifying your security team of the potential breach.
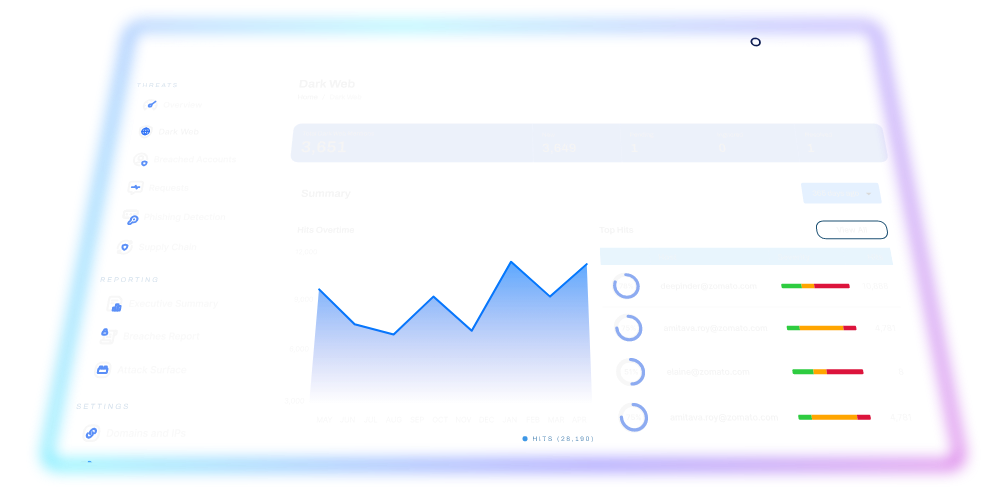
Advanced Dashboard Features
For Comprehensive Monitoring
DeXpose offers an intuitive and powerful dashboard equipped with a range of features designed to provide you with unparalleled control and insight into the security of your digital landscape. From monitoring domains to detecting compromised credentials across various user segments, our dashboard empowers you to take proactive actions against potential threats.
Multi-Domain Monitoring
Stay on top of your organization's digital footprint effortlessly. Our dashboard enables you to monitor all domains associated with your business from a single, centralized interface. This ensures that no potential security gaps go unnoticed.
VIP Personal Email Monitoring
Personal accounts can serve as entry points for cyberattacks. Our dashboard enables you to monitor VIP personal email addresses, extending your security net to protect even the most sensitive communications.
End User Focus
DeXpose goes beyond protecting just your employees. Our platform is designed to detect compromised credentials related to all end users, including partners, clients, and customers. This comprehensive approach ensures that every point of entry is safeguarded.
Vendor And Supply Chain Risk View
Protecting your organization also involves securing your extended network. DeXpose's dashboard provides a risk view of your vendors and supply chain, allowing you to identify and address potential weak links in your cybersecurity chain.
Actionable Insights
The platform doesn't just provide data; it delivers actionable insights. You can directly manage detected compromised credentials, enabling you to take swift and informed action to secure your accounts.
Customizable Reports
Stay informed at a glance with reports tailored to your needs. Create daily, weekly, and monthly executive and technical reports that provide a snapshot of compromised credentials detected, actions taken, and potential threats mitigated.
Our dashboard isn't just a monitoring tool; it's a proactive shield that empowers you to make informed decisions, safeguard your organization's digital assets, and maintain trust in an increasingly complex cybersecurity landscape. Experience the power of DeXpose's advanced dashboard and elevate your cybersecurity strategy today.

Reputation Protection
Safeguard your organization's reputation by preventing leaks of sensitive information.
Compliance
Strengthen compliance efforts by actively monitoring and addressing security vulnerabilities.
Prevent unauthorized access and data breaches by securing accounts linked to compromised credentials.
Proactive Security
Stay ahead of cyber threats by identifying compromised credentials before they are misused.
