Summary
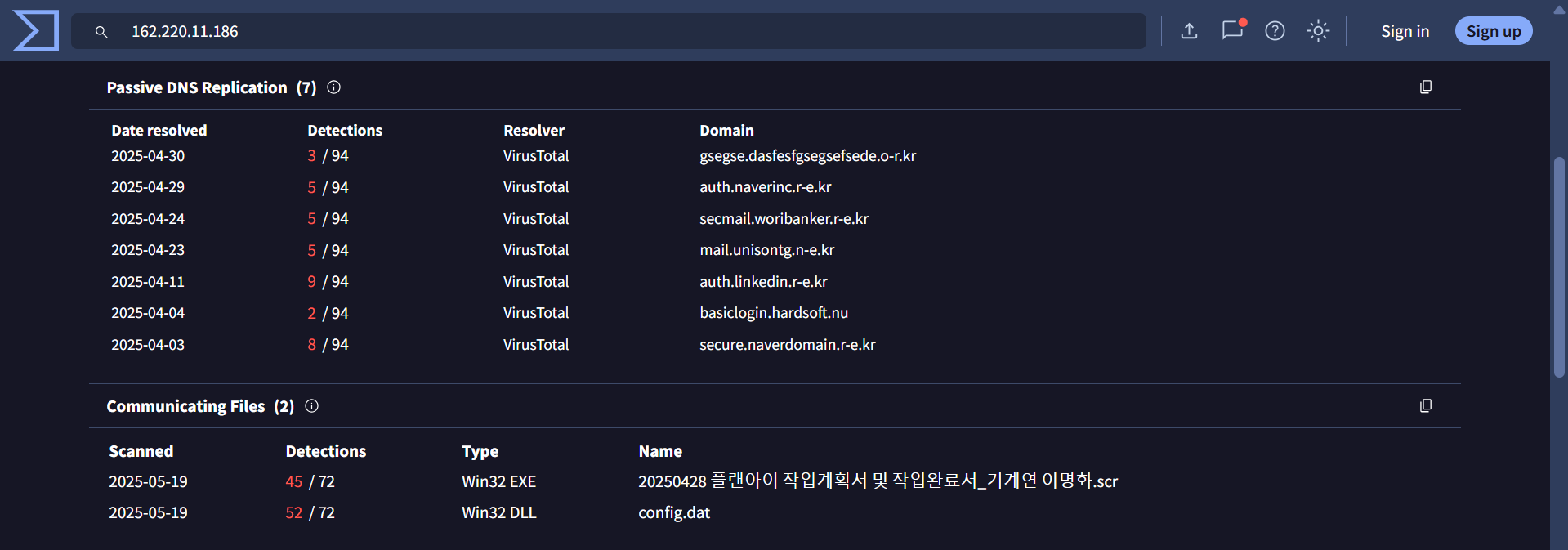
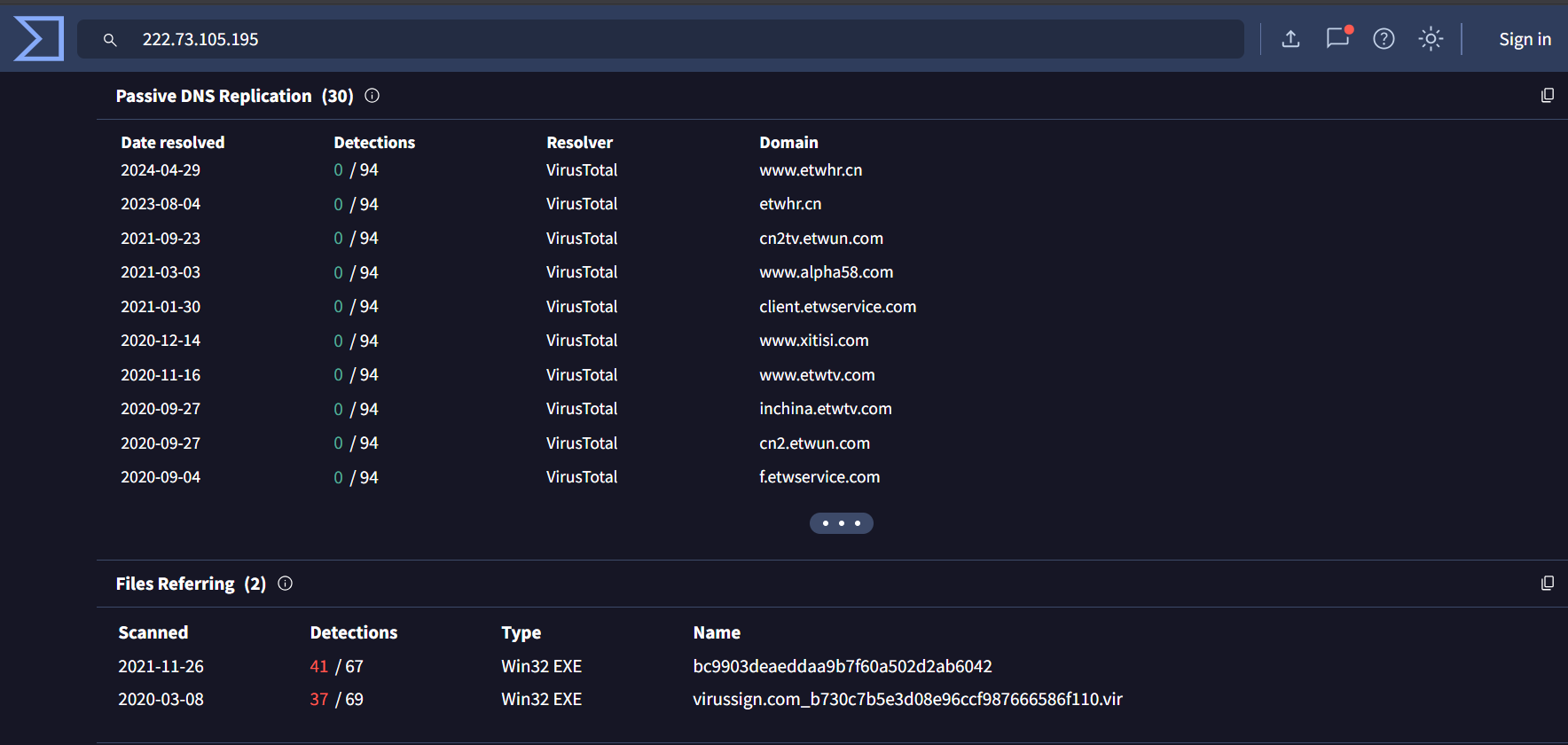
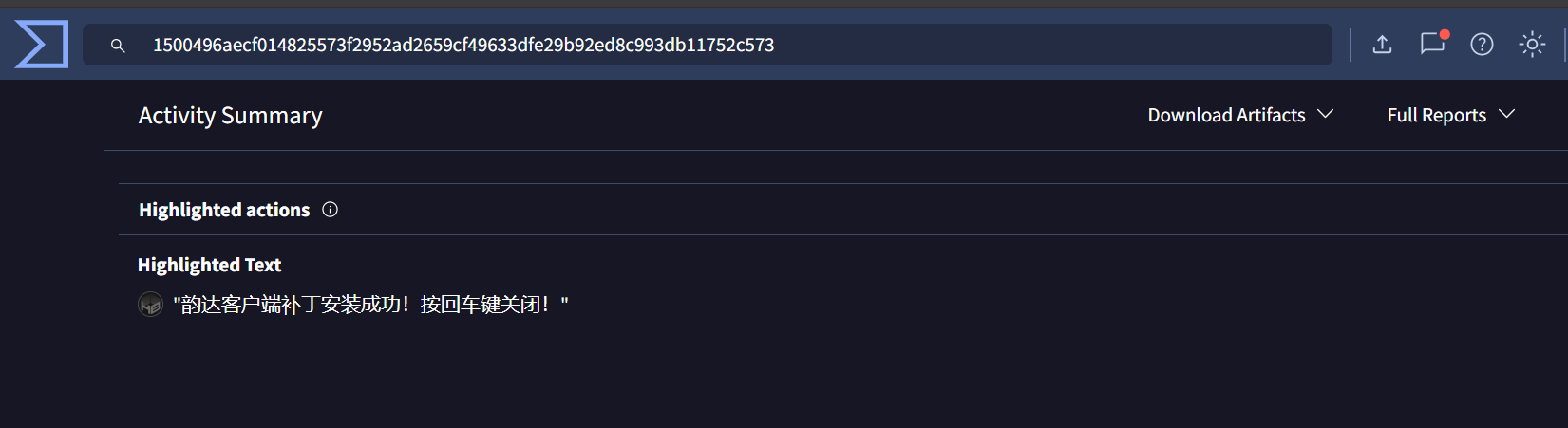
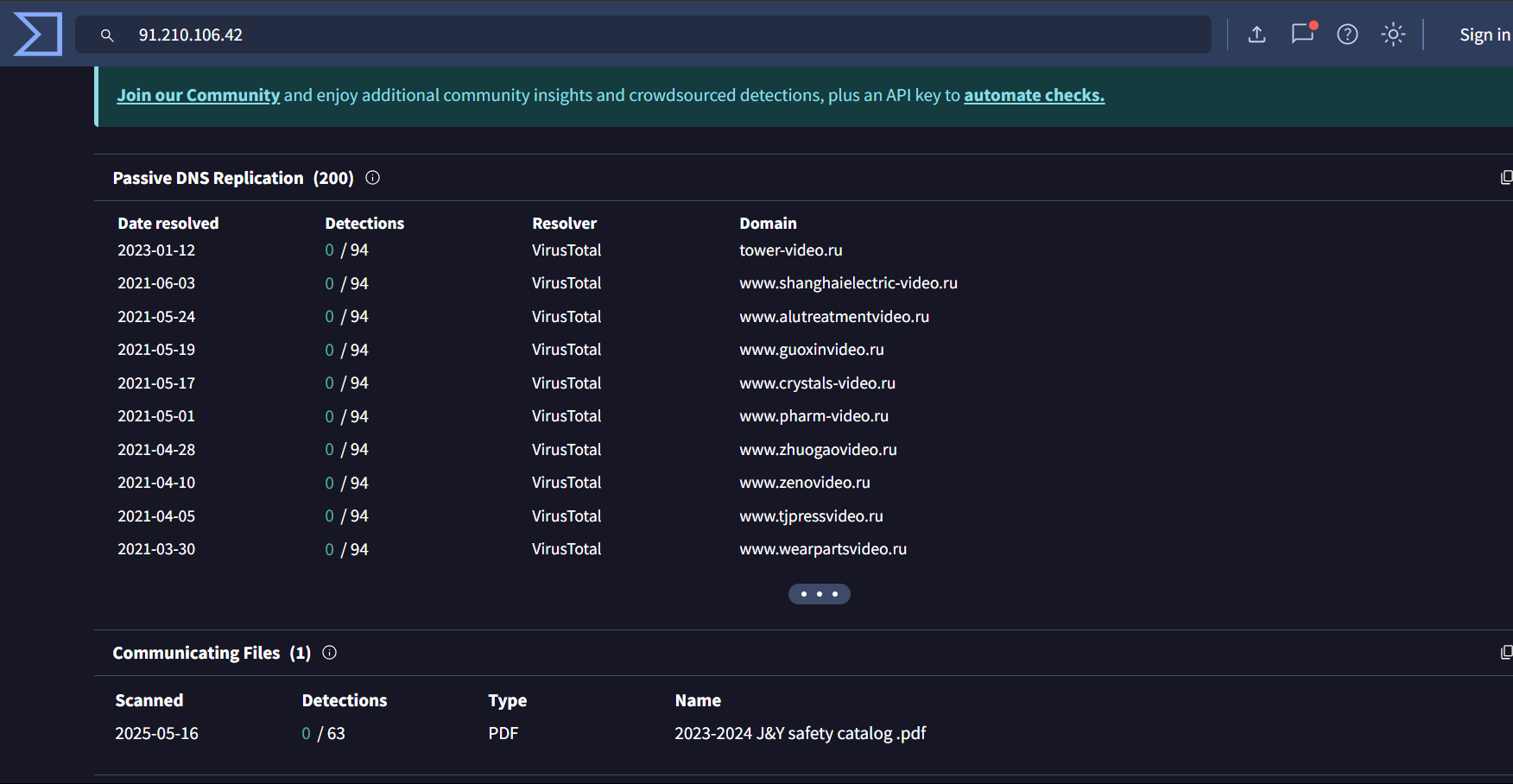
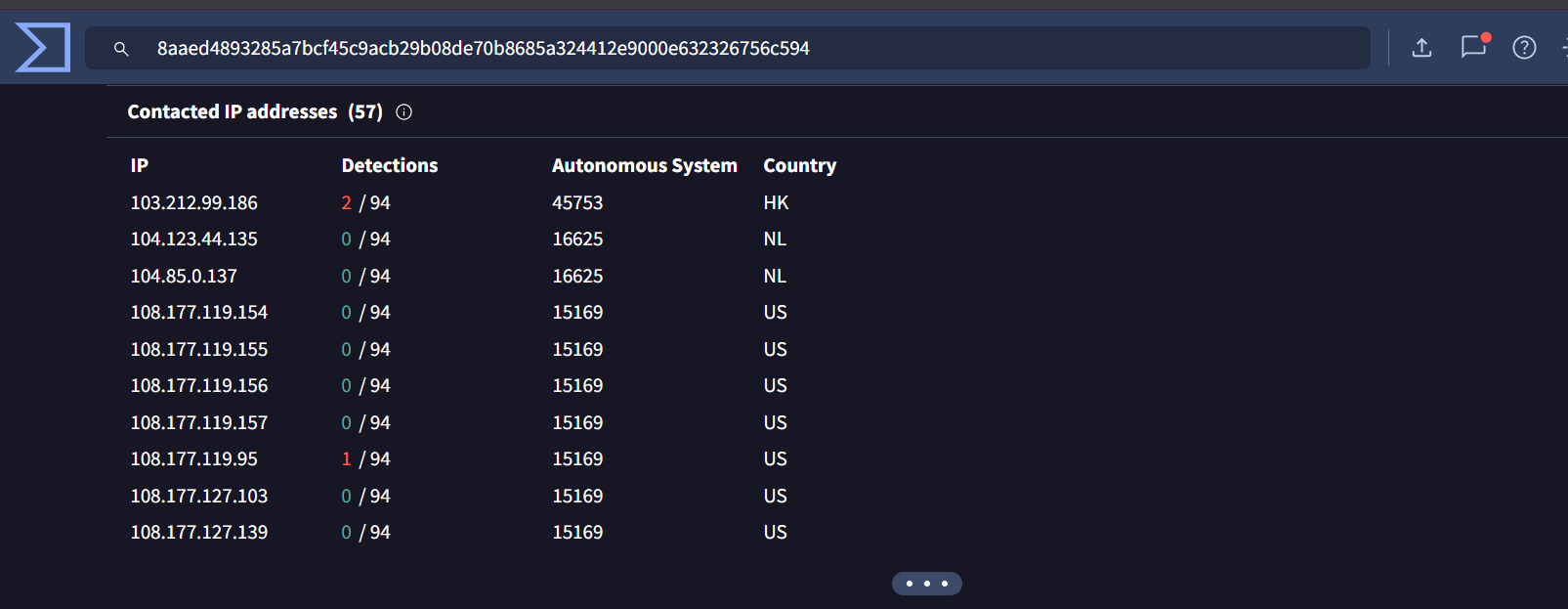
Recently identified previously undetected Kimsuky (also known as Black Banshee) infrastructure through advanced pivoting techniques. Using HTTP header analysis, SSL Cert and JARM fingerprinting. We uncovered several IPs and domains, many of them were not flagged by VirusTotal at the time of discovery.
Who is APT43 Kimsuky / Black Banshee?
Kimsuky, also known as Black Banshee, is a North Korean state-sponsored APT group active since at least 2012. The group is primarily focused on cyber espionage, targeting organizations related to foreign policy, defense, and national security.
Target Sectors:
- Government and defense
- Think tanks and research institutions
- Media organizations
- Nuclear and energy sectors
- NGOs and academic entities
Geographic Focus:
- South Korea
- United States
- Europe
- United Nations-related organizations
Phishing Tactics:
- Spear-phishing with highly tailored lures (often impersonating journalists, scholars, or official entities)
- Use of malicious Microsoft Office documents or compressed archives
- Embedded macro scripts and remote template injection
- Credential harvesting through spoofed login pages and malicious links
Notable Techniques:
- Social engineering via email or messaging platforms (e.g., Gmail, Outlook, Telegram)
- Use of compromised legitimate infrastructure for C2 communication
- Browser data theft and keystroke logging
- Abuse of cloud services (e.g., Google Drive) for data exfiltration
Initial Pivot
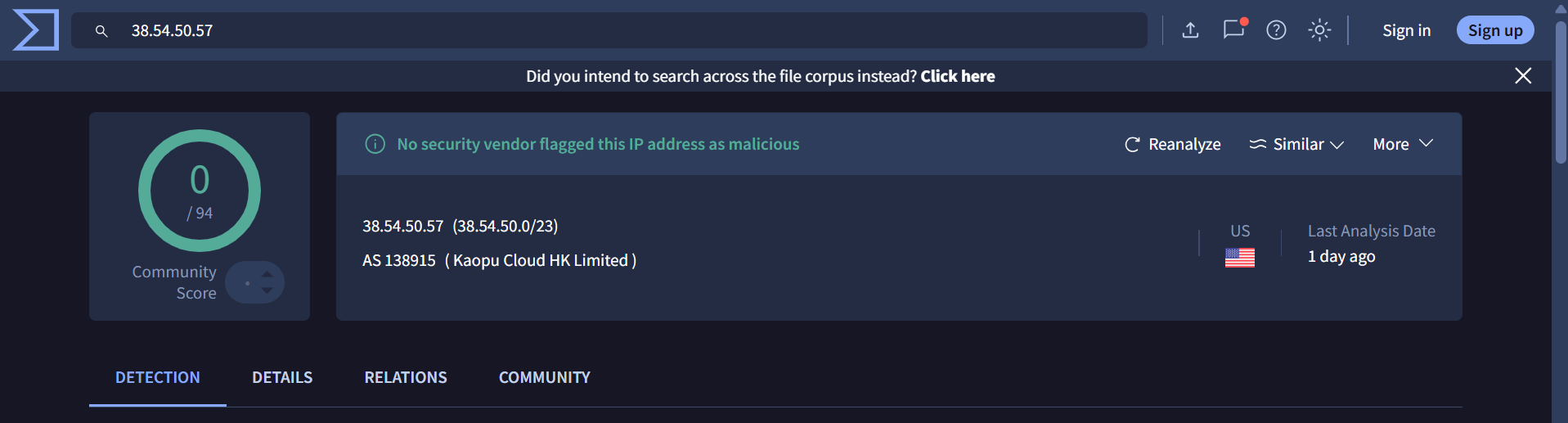
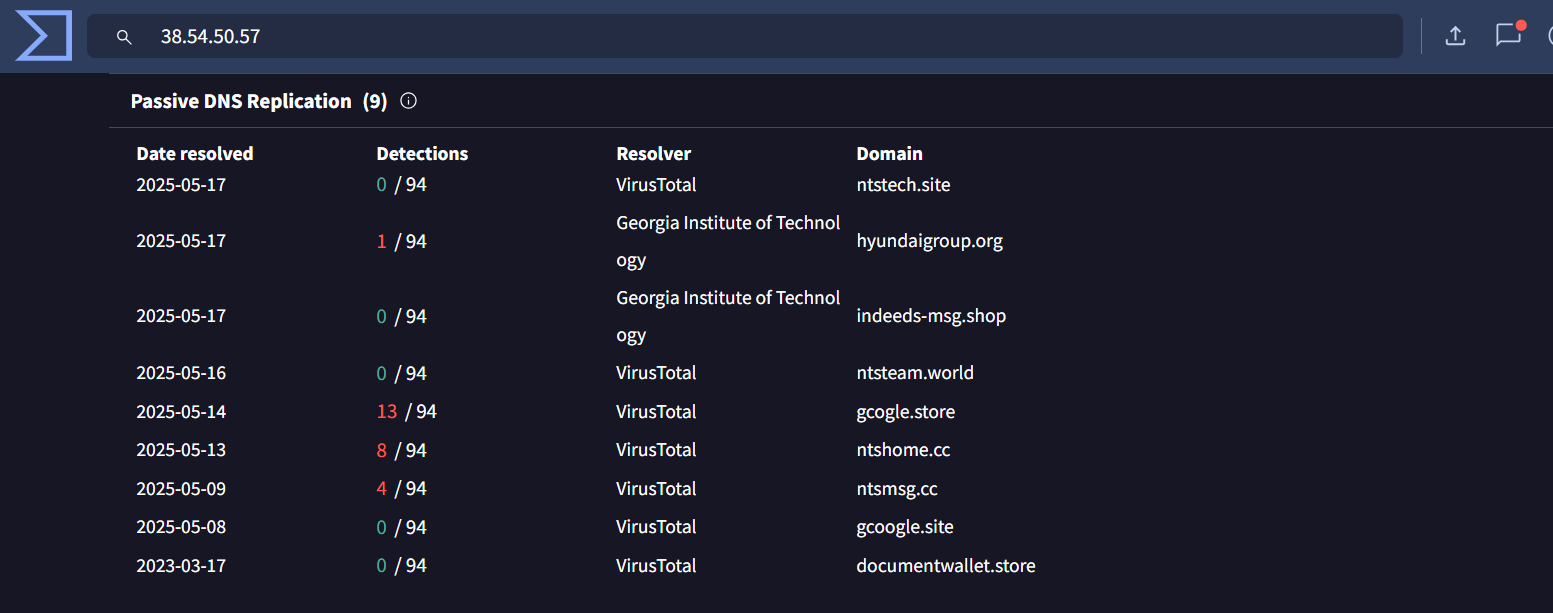
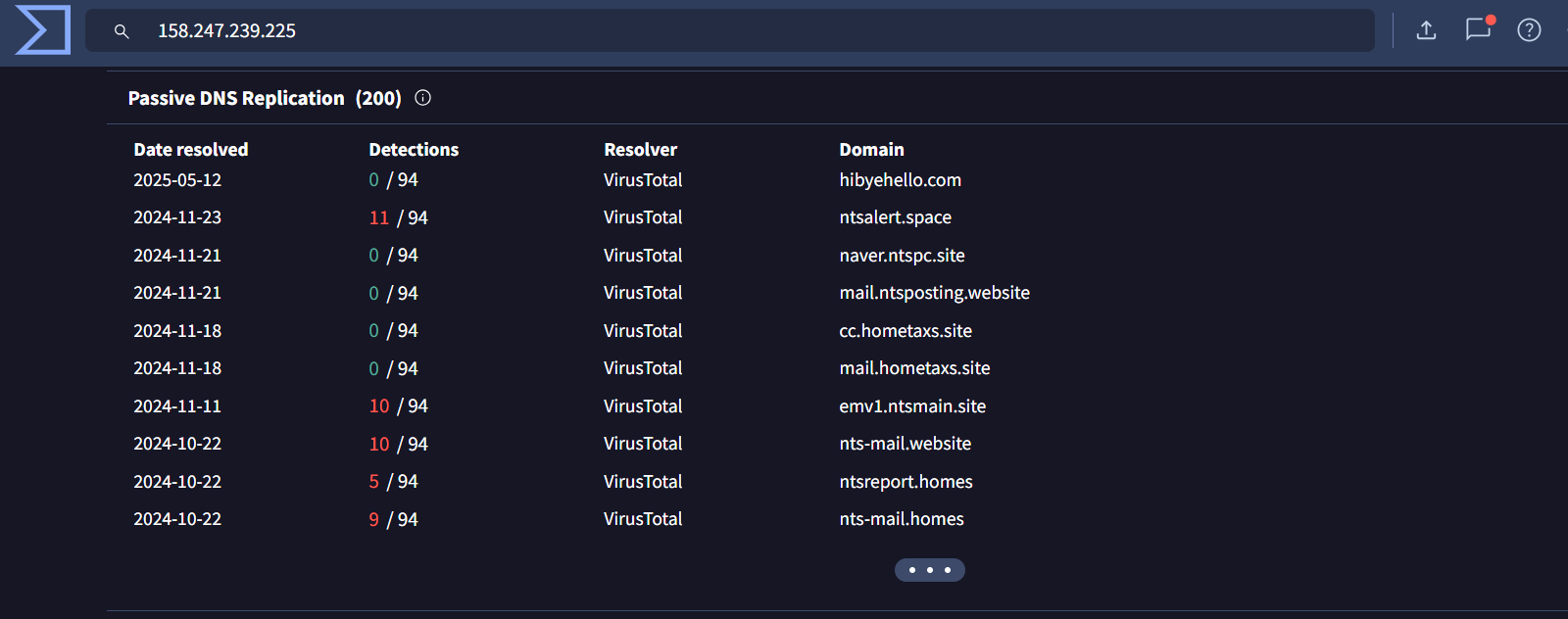
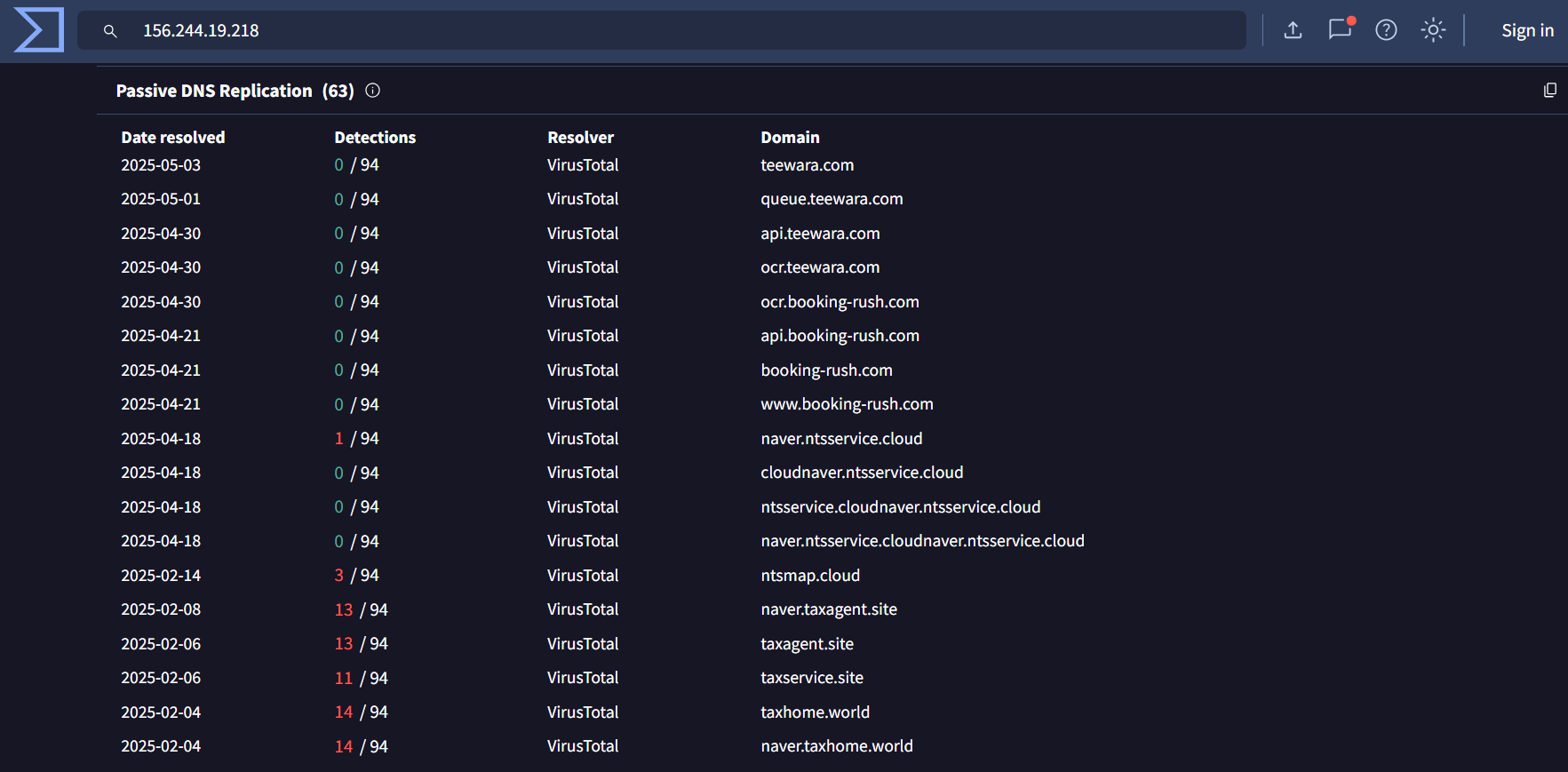
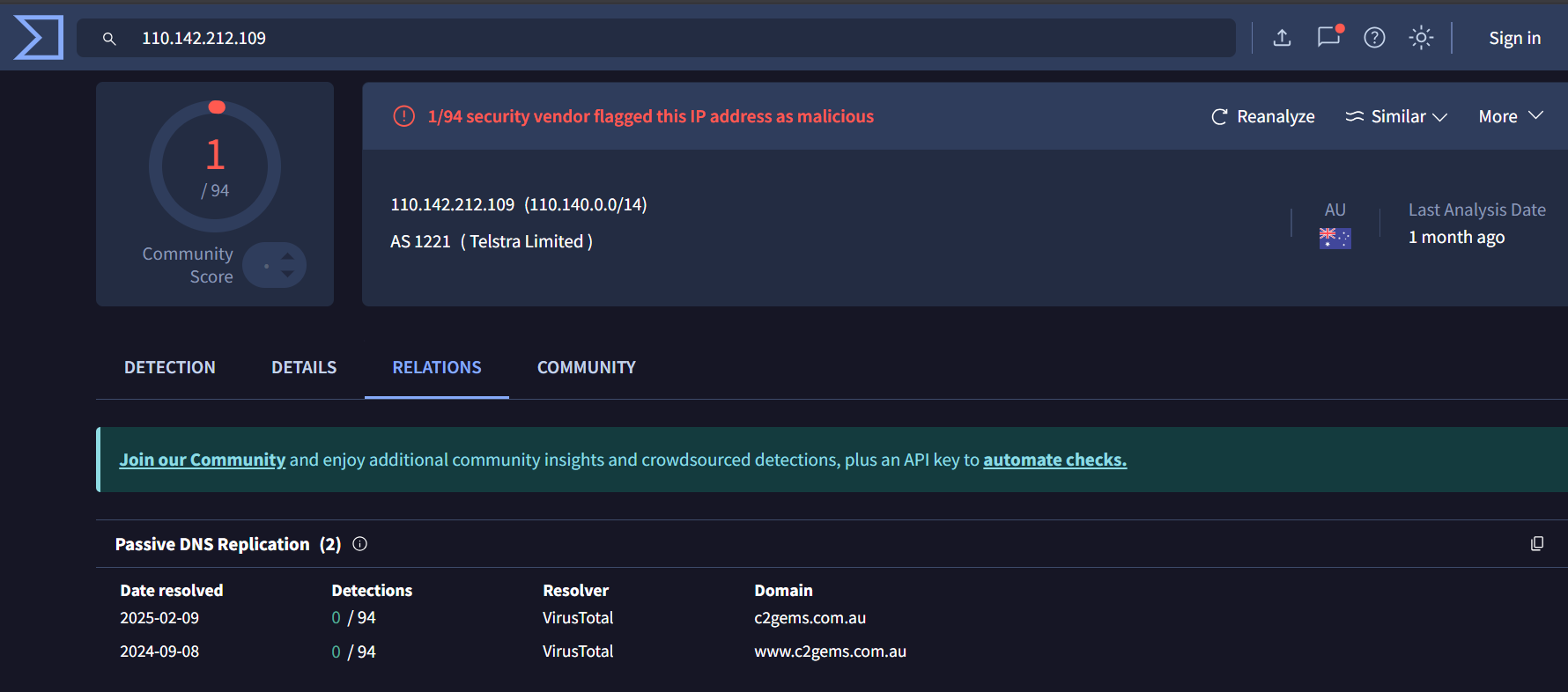
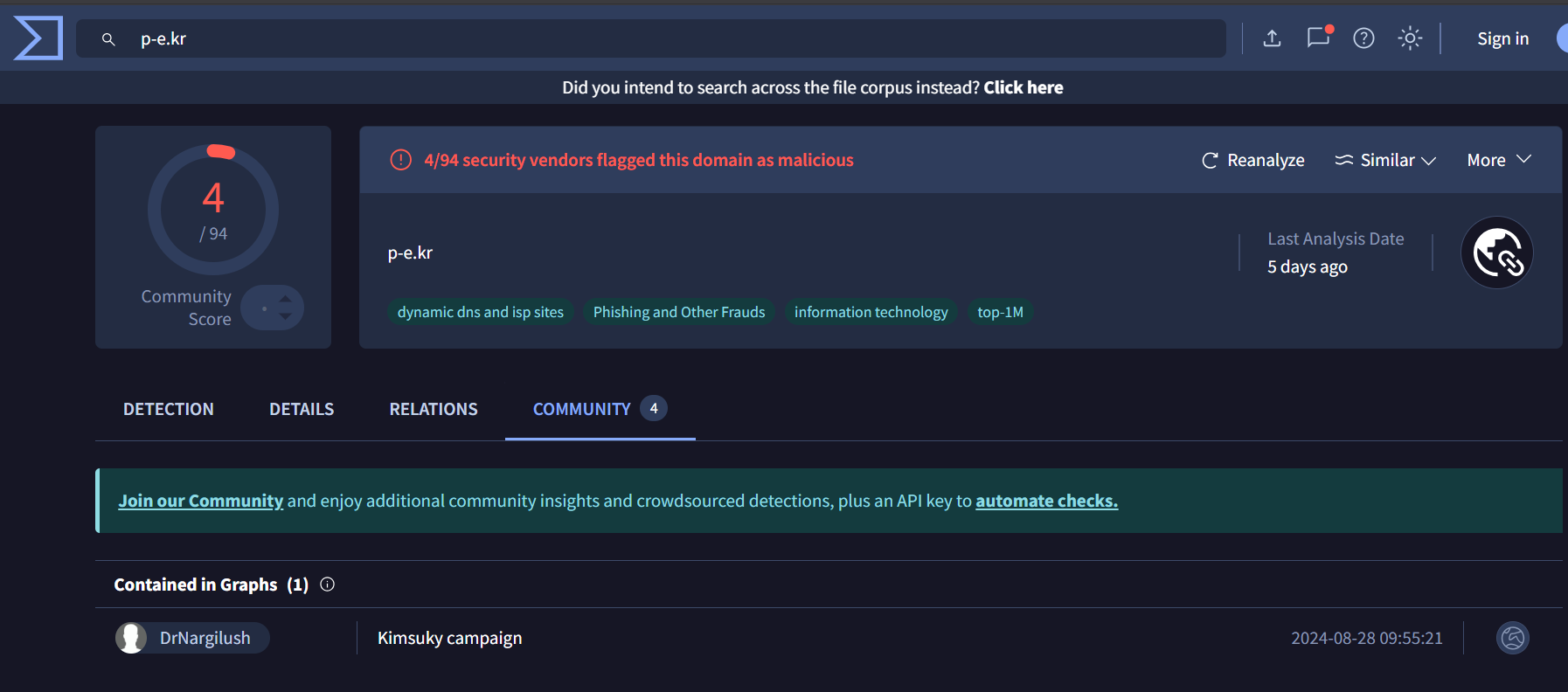
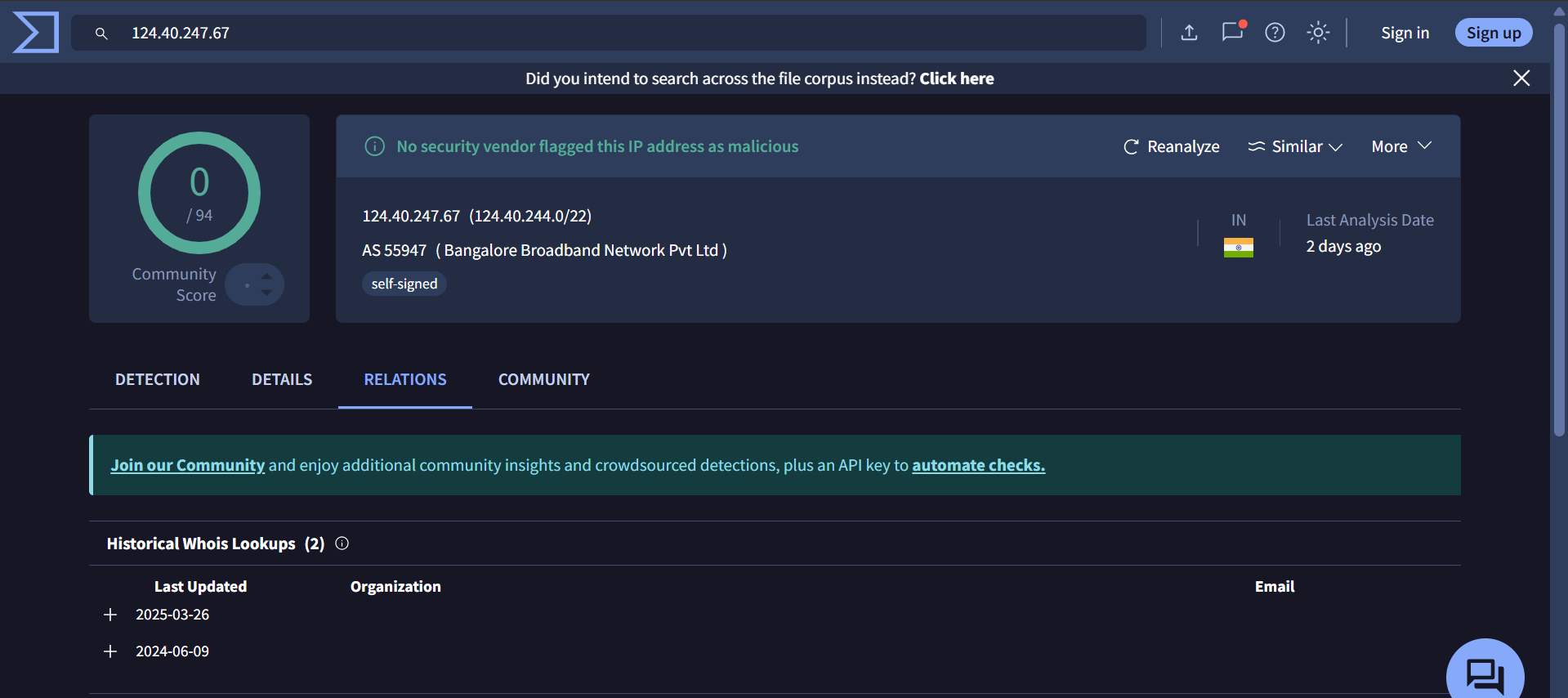
The initial pivot point for this hunt are IP addresses 158[.]247[.]239[.]225 and 67[.]217[.]62[.]219 as they are attributed to Kimsuky
We will pivot using HTTP header, JARM and Certificate public key
158[.]247[.]239[.]225