Researches, News, and more
DeXpose Blog
Cybercrime Statistics 2026 (Updated) | Global Trends, Data Breaches, AI Risks & Future Threats
Cybercrime in 2026 is best understood as two intertwined phenomena: (1) cyber-enabled fraud at a societal scale (phishing, impersonation scams, payment/invoice fraud, investment fraud) and (2) intrusion-driven crime against organisations (credential abuse, exploitation of vulnerabilities,…
Dark Web Sites List | Safety, Legality, Risks and Trusted Platforms
Dark web sites are websites hosted on encrypted networks like Tor that require specialized browsers to access. While some support privacy, journalism, research, and secure communication, others are associated with cyber threats and fraud. Today,…
IoT Hacking Statistics 2026 | Global Trends and Key Insights
The world of connected devices faces a new wave of cyber threats in 2026. This report breaks down the latest IoT hacking statistics and trends, comparing 2026’s early indicators with the alarming growth seen in…
Deep Web vs Dark Web: A Clear Guide to Access, Risks, and Security
Deep Web: What It Means (and Why You Use It Daily) The deep web is a considerable portion of the internet that search engines don’t list. Think of content that sits behind a login, subscription,…
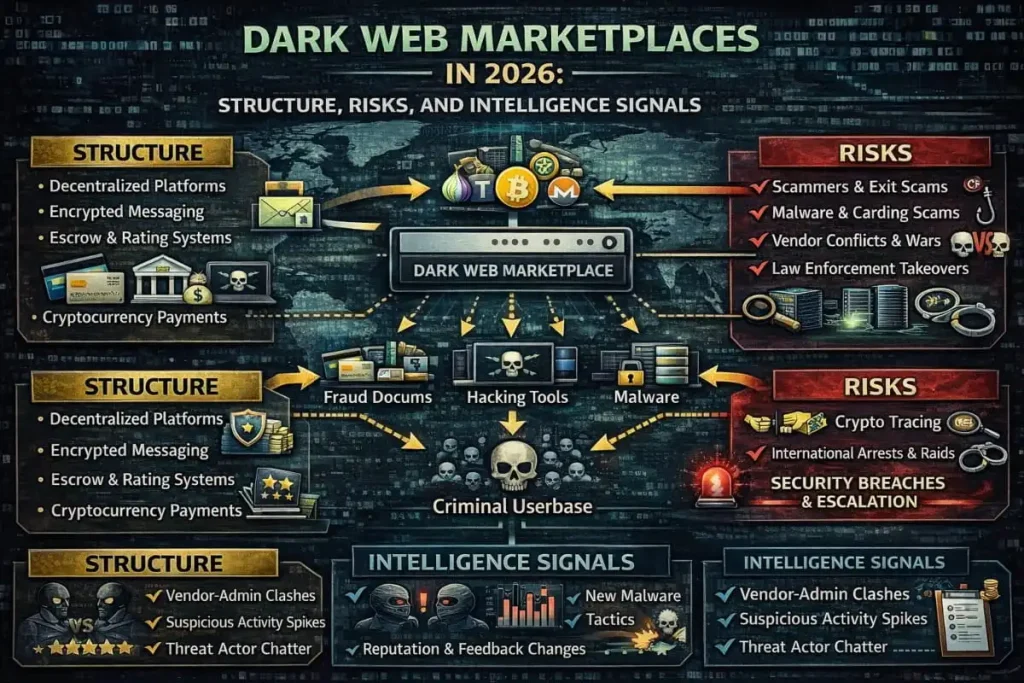
Dark Web Marketplaces in 2026 | Current Status and Why They Matter
Despite major law enforcement takedowns, the dark web ecosystem remains active in 2026. A small number of dominant marketplaces continue to facilitate illicit trade, adapting quickly to seizures, arrests, and infrastructure shutdowns. Current Landscape As…
What Is the Dark Web? Scale, Trends & Growth (2026 Report)
When people ask what the dark web is, they’re referring to the hidden part of the internet that can only be accessed using special software like the Tor browser. Designed for anonymity, it enables private…
Telegram Dark Web Explained (Risks, Real Uses & How to Stay Safe)
Telegram scams are increasingly tied to a dark web lite ecosystem where criminals use Telegram channels and massive Telegram groups to operate underground markets with speed and reach. Instead of relying only on Tor-based dark…
Top Dark Web Search Engines 2026 (Safe + Secure Guide)
The dark web isn’t “the internet, but darker.” It’s a separate slice of the web that lives on anonymity networks (most commonly Tor) and uses addresses like .onion that normal browsers and search engines don’t…
Brand Protection Solutions to Stop Counterfeits and Online Fraud
Counterfeits and online fraud steal sales, damage trust, and erode hard-won reputation. Effective brand protection solutions must catch fake listings, detect credential leaks, and stop fraud before it spreads. In this post, we explain how…
Why Brand Protection Is Essential in Today’s Digital World
In a noisy online world, your name, logo, and reputation can be copied, misused, or attacked in minutes. That is why brand protection matters right now. A clear brand protection design stops counterfeit goods, phishing,…
What Is Dark Web Monitoring and How Does It Help Protect You
If you’ve ever worried about your email, passwords, or business data being sold online, you’ve probably wondered, what is dark web monitoring, and how can it help protect you? Dark web monitoring watches hidden corners…
A Guide to Cyber Threat Management and Threat Intelligence Platforms
Cyber threats keep changing, and defending against them takes more than one-off fixes. Cyber Threat Management must be a continuous program that blends innovative tools, transparent processes, and human judgment. In this guide, you’ll get…