In a noisy online world, your name, logo, and reputation can be copied, misused, or attacked in minutes. That is why brand protection matters right now. A clear brand protection design stops counterfeit goods, phishing, and reputation damage before they spread, and it keeps customers confident that they’re buying from the real you.
Why brands are more exposed than ever
Customers discover businesses across more zones than ever: search, marketplaces, social apps, messaging, and new storefronts. That reach helps sales, but it also multiplies risk, making strong cyber threat management essential. Today’s attackers use automation, low-cost online storefronts, stolen credentials, and the dark web to copy logos, steal listings, or impersonate support channels. A single viral post or fake listing can erode trust and cost real revenue.
Quick examples of common harms
- Fake development listings on marketplaces that look like yours
- Phishing pages using your logo to steal customer logins
- Stolen credentials sold on hidden forums
- Negative reviews and reputation attacks by contestants or criminals
Each of these harms erodes trust and makes customers hesitate. Stopping them early is what separates a resilient company from a vulnerable one.
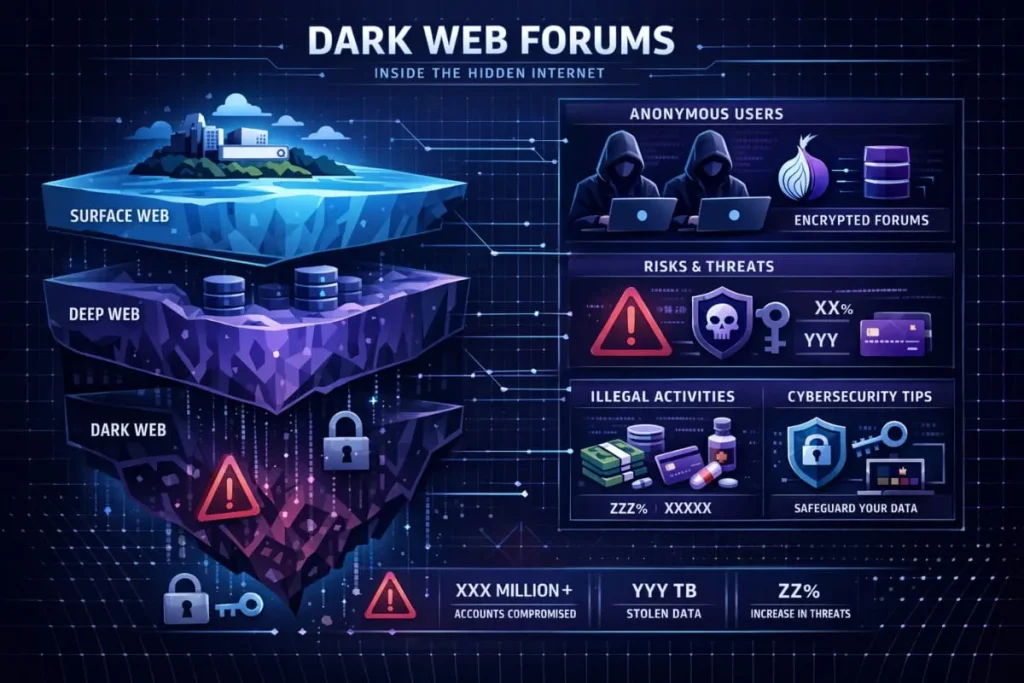
How threat sources work: surface, deep, and dark web
Think of online risk as three layers. The surface web is public pages and marketplaces. The deep web includes private forums and databases. The dark web is where stolen credentials and forged documents trade hands.
Tools and processes that monitor the deep and dark layers can spot threats before they hit public channels. That’s why businesses lean on Dark Web Monitoring and open investigations into leaked data. If someone finds your admin password on an undercover forum, they might try account takeover or post counterfeit goods pretending to be you.
Key components of an adequate protection program
Visibility and monitoring
You can’t protect what you can’t see. Monitoring includes:
- Marketplace monitoring for fake listings
- Social media scans for impersonations or copycats
- Domain and trademark watch to detect lookalike sites
- Dark Web Monitoring to find leaked credentials and stolen assets
Using automated detection and human consideration helps keep false positives low and response times fast.
Threat intelligence and context
Alerts alone are noise. Threat intelligence turns alerts into action by telling you:
- Who’s behind a campaign (if known)
- Whether the activity is targeted or opportunistic
- How widespread the issue is
A Threat Intelligence Platform helps collect and formalise signals so your team can act with confidence.
Fast takedown and enforcement
Once you verify an abuse, act fast. Takedown steps include sending policy notices to marketplaces, filing DMCA or trademark takedowns, and contacting hosting providers. Having templates and escalation courses cuts time and prevents problems from going viral.
Prevention and hardening
Prevention is about making attacks harder. That includes:
- Strong account security and multi-factor authentication
- Routine checks to check email data breache and respond to leaks
- Employee training to spot social engineering attempts
Legal, policy, and partnerships
Work with legal counsel, registrars, and platform communications. A Cybersecurity partnership with specialists speeds response and gives you leverage when platforms dispute a takedown.
The role of technology: tools that matter
Dark Web Monitoring and digital risk tools
Dark Web Monitoring finds stolen credentials and references to your brand on hidden forums. Paired with a Free Dark Web Report or a free dark web scan, you can quickly assess whether your data is exposed. Some free Dark Web Monitoring tools give a basic view; paid services go deeper and tie findings to remediation steps.
Threat Intelligence Platform
A Threat Intelligence Platform aggregates signals from many sources and helps analysts prioritise threats. It connects to open sources, commercial feeds, and internal telemetry so you can track campaigns, phishing kits, and actors.
Credentials Leak Detection
Credentials Leak Detection focuses on user credentials. When a leak is found, teams can force password resets, lock accounts, and notify affected users. This reduces the chance of account takeover and fraud.
Open Source Intelligence
Open Source Intelligence, or OSINT, helps investigators gather public clues: social accounts, domain registrations, and informed documents. OSINT often supplies the context necessary to prove abuse and support takedown requests.
Digital risk protection platforms
Digital risk protection tools watch many sources at once: social, marketplaces, app stores, and the dark web. They supply alerts, risk scores, and workflows so a small team can manage a large footprint.
Mapping specific threats to solutions
Counterfeit goods and marketplace fraud
Threats: Fake listings, knockoff products, unauthorised resellers.
Solutions: Marketplace monitoring, trademark enforcement, seller verification, and rapid takedowns.
Phishing and brand impersonation
Threats: Fraudulent emails, cloned websites, fake customer support chats.
Solutions: Threat Intelligence Platform to stain phishing kits, DMARC/SPF/DKIM to reduce spoofed email, and public takedowns of scam pages.
Leaked credentials and account takeover
Threats: Stolen passwords used to access vendor portals or internal apps.
Solutions: Credentials Leak Detection, caused resets, and monitoring the dark web for compromised accounts.

Reputation attacks and fake reviews
Threats: Bot-driven negative reviews or false claims.
Solutions: Review monitoring, legal escalation, and proactive customer communications.
Data exposure and leakage
Threats: Internal documents or customer records posted publicly.
Solutions: Data discovery, Open Source Intelligence to discover leaks, and incident response that includes notification and containment.
Brand protection services: what to expect
If you hire outside help, look for teams that combine legal, technical, and investigation skills. Brand protection services should offer:
- Continuous monitoring across channels
- Investigation of findings with human analysts
- Takedown and enforcement actions with confirmation packages
- Regular reporting and KPIs so you can measure impact
A good provider will help you set policy, tune alerts, and build internal playbooks so your team can act quickly.
Brand protection solutions: choosing tech and vendors
When evaluating vendors, prioritise solutions that:
- Integrate with your existing security stack
- Provide clear workflows for verification and takedown
- Offer APIs and automation for fast action
- Support both proactive monitoring and reactive takedowns
Ask for real examples, request a demo with your assets, and test the vendor’s ability to deliver results on a trial case.
Practical steps to start today
Step 1: Inventory your assets
List your domains, subdomains, consequence names, logos, trademarks, social accounts, and key executives. This inventory is the foundation of your brand protection solutions and ongoing monitoring.
Step 2: Enable introductory email and domain protections
Set up DMARC, SPF, and DKIM to reduce email spoofing. Register common typo domains and monitor them for abuse.
Step 3: Run a free dark web scan and review results
Use a free dark web scan or order a Free Dark Web Report to see if any credentials or customer data are exposed. Even a basic scan gives valid leads.
Step 4: Choose a monitoring mix
Combine in-house checks with vendor services for broad coverage. Use automated scans for volume and human analysts for high-value incidents.
Step 5: Build a takedown playbook
Create templates for takedown notices, demarcate who signs them, and set SLAs. Include legal steps for marketplaces and hosting providers.
Step 6: Train people and run tabletop drills
Simulate an impersonation or leak and practice your response. Training reduces confusion and speeds remediation in real incidents.
How to measure success
Track these KPIs to show progress:
- Time to detect negative listings or impersonation
- Time from detection to takedown or mitigation
- Number of counterfeit listings removed each month
- Reduction in phishing click-throughs and account takeovers
- Customer trust metrics and complaint volumes
Good dashboards let you spot trends and justify investment.
Building the right team
You need a mix of roles:
- Brand protection leads to a management strategy
- Analysts for monitoring and investigation
- Legal counsel for takedowns and enforcement
- IT and security for credential handling and incident response
- Communications for customer-facing messages
Where internal headcount is limited, a Cybersecurity partnership with an experienced provider can fill gaps.
Standard tools and tests to add to your stack
- Domain and SSL monitoring to detect rogue sites
- Marketplace scraping for product listings
- Dark Web Monitoring for leaked credentials and discussions
- Open Source Intelligence for attribution and context
- Regular checks to check email data breaches and force resets when needed
Consider running a free dark web scan monthly, and build routines around verification and escalation.
Dark web: practical notes and options
Not every mention on the dark web is an instantaneous danger—context matters. Criminal forums sometimes post old credentials or talk without intent. A structured investigation distinguishes active campaigns from chatter.
Companies often use a dark web monitoring solution to automate searches, then assign analysts to verify relevance. When high-risk items appear, act fast to contain damage.
If budgets are tight, free Dark Web Monitoring tools and a complimentary dark web scan can provide a low-cost starting point. They surface obvious leaks quickly, but they don’t replace a complete service when high-value assets are at risk.
When to bring in external help
Bring in a specialist when:
- You see a large-scale leak or credentials published publicly
- Counterfeits are appearing across many marketplaces
- You need legal takedowns in multiple countries
- Your internal team lacks experience with threat actors
A provider can speed response and handle cross-platform escalation.
Legal enforcement and policy playbook
Legal steps vary by country. Enforcement options include:
- Trademark or copyright takedown notices
- DMCA paperwork for copyrighted images and development descriptions
- Domain dispute processes for cybersquatting.
- Civil litigation, when necessary
Work with legal counsel to create standard templates and keep jurisdiction requirements in mind.
Real-world scenario: quick tabletop example
Situation: A popular product page shows a bogus item that uses your product photos and logo. Customers report fake items arriving that lack a warranty.
Response steps:
- Verify the listing and capture screenshots and URLs.
- Run a quick credentials check and a free dark web scan to see if seller accounts are tied to leaked credentials.
- Send a takedown notice to the marketplace with proof of brand ownership.
- Notify customers and issue guidance about how to spot authorised sellers.
This simple loop shows how monitoring, verification, takedown, and communication work together.
Budgeting and ROI
Brand protection often looks like a cost until you compare the alternatives. Lost sales, refunds, legal fees, and harmed reputation add up. Build a modest budget for monitoring and a clear escalation plan. Track cost per incident removed versus cost of lost revenue to justify ongoing spend.
Common myths about brand protection
Myth 1: No one will copy our brand.
Reality: If you sell anything online, you’re a target.
Myth 2: Takedowns solve everything.
Reality: Takedowns help, but repeat criminals and new storefronts appear fast. Continuous monitoring is required.
Myth 3: Free tools are enough.
Reality: Free tools reveal some issues but often miss the context and scale that paid services provide.
Checklist: a simple starter list
- Inventory domains, trademarks, and social handles
- Select DMARC, SPF, and DKIM for email protection.
- Run a free dark web scan and get a Free Dark Web Report if available.
- Deploy marketplace and social monitoring feeds.
- Establish takedown templates and SLAs
- Run quarterly tabletop exercises with your team or vendor.
Putting it all together: an example protection flow
- Automated monitor flags a suspicious listing.
- Analyst verifies and enriches the alert using Open Source Intelligence.
- Team checks for leaked certificates via Credentials Leak Detection.
- If verified, Legal sends a takedown, and the vendor suspends the listing.
- Communications notifies affected customers and updates guidance.
This flow reduces friction and ensures action is repeatable.
Choosing between in-house and managed services

In-house works if you have the people and budget to run continuous monitoring, investigations, and legal follow-up. Calmed services are best when you need scale, 24/7 monitoring, or international enforcement.
Ask vendors for a trial focused on a narrow scope of your assets. Evaluate the clarity of their reports, speed of action, and the quality of their proof packages.
How to prepare for the next wave of threats
Threats evolve. Prepare by:
- Building relationships with marketplaces and hosting providers
- Automating routine checks, but keeping mortal review for high-value incidents.
- Regularly training employees on social engineering and phishing.
- Maintaining a tested incident response plan
A proactive posture reduces the chance of viral damage.
Conclusion
The digital world brings growth and risk in equal action. Solid brand protection blends monitoring, threat intelligence, Dark web email scan, legal enforcement, and transparent processes. Start with visibility, add prevention, and make sure you can act fast when something goes wrong. Investing in a program now protects revenue, reputation, and customer trust for years to come.
Brand protection is not optional. It is a business function that protects your most visible asset: your reputation.
FAQs
How fast should I respond to a counterfeit listing?
Respond within hours when the listing affects customers or uses your brand assets. Quick action limits the spread, reduces orders of counterfeit goods, and protects the reputation.
Are free dark web scans functional?
Yes, they’re a good starting point to find prominent leaks. For higher-risk cases, pair them with paid monitoring and human analysis.
What is the first thing to do after finding leaked employee credentials?
Contain by forcing password resets and enabling multi-factor authentication, then investigate the scope and notify involved parties as required.
Can legal takedowns remove an impersonator permanently?
Takedowns stop a specific instance fast, but repeat offenders or new domains can appear. Continuous monitoring and enforcement are needed.
Should brand protection live in legal, security, or marketing?
It’s cross-functional. Legal handles takedowns, security handles credentials, and marketing handles customer trust. A central owner or Cybersecurity partnership coordinates all three.