Researches, News, and more
DeXpose Blog
Reputation Management Strategies for Modern Businesses
In today’s hyperconnected world, a unmarried customer review, viral post, or security lapse can ripple across markets overnight. Reputation Management is no longer optional it’s a strategic capability that protects revenue, talent, and long-term growth.…
Email Data Breach Scan: Check If Your Info Is Exposed
Your email address is the primary key to your digital life from social apps and subscriptions to banking reset links. Running an Email data breach scan early is one of the fastest ways to find…
Discover Hidden Threats Claim Your Free Dark Web Report
In an age where personal and business data move faster than ever, uncovering hidden exposure on underground markets is critical. A Free Dark Web Report can quickly reveal whether your email addresses, passwords, or proprietary…
Protect Your Data with Advanced Deep Web Scanning
In an era when personal and corporate data fuels both invention and crime, protecting what matters requires more than basic antivirus software. Deep Web Scanning uncovers hidden risks where conventional search engines can’t reach, helping…
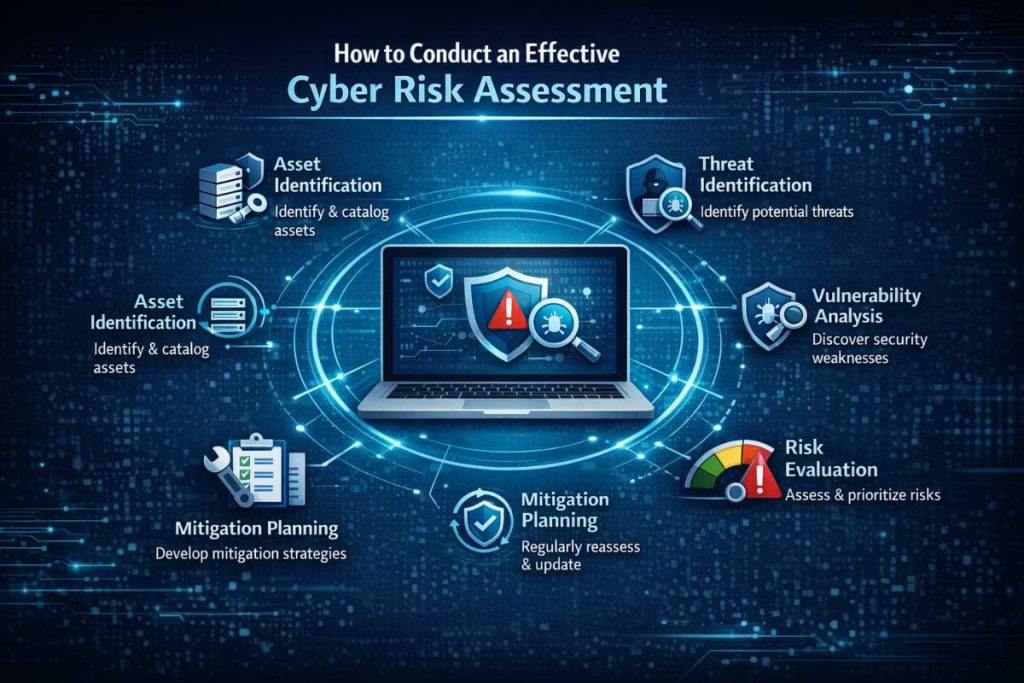
How to Conduct an Effective Cyber Risk Assessment
In today’s digital-first world, organizations rely heavily on interconnected systems, cloud services, and third-party vendors. While this digital transformation creates enormous opportunities, it also expands the potential attack surface. One of the most important steps…
Data Leakage Protection How to Secure Sensitive Business Data
Data Leakage Protection is the foundation of any modern information security program. From customer documents to strategic plans, businesses hold sensitive data that can destroy trust and revenue if exposed. This post walks through practical,…
Cyber Threat Management Guide for a Secure Digital Future
In today’s hyper-connected world, the way organizations operate has shifted dramatically, with digital platforms serving as the backbone of business continuity. While this transformation brings speed, convenience, and scalability, it also introduces complex challenges. Among…
Oracle Breach Check Instantly See If Your Data Is at Risk
In today’s hyperconnected digital world, the security of enterprise platforms is no longer an afterthought it’s a business-critical priority. With vast amounts of exposed data stored in cloud environments, even a single breach can have…
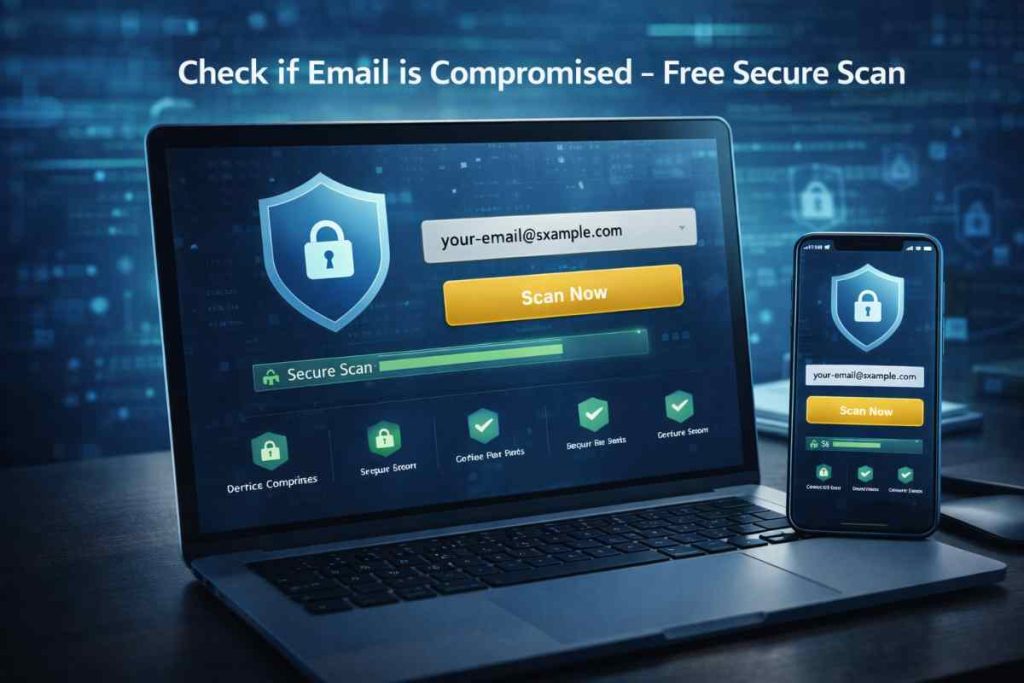
Check if Email is Compromised Free Secure Scan
Email is the backbone of our digital identity. It’s the account you use to sign in to social networks, online banking, e-commerce stores, business applications, and almost every modern service. Suppose someone gains unauthorized access…
How to Protect from Ransomware Attack Security Guide
In recent years, ransomware has evolved from a rare cyber nuisance into one of the most disruptive and costly forms of cybercrime. The number of ransomware incidents continues to climb, with attackers targeting everything from…
What Is Digital Risk Protection? The Complete Guide for 2025
In today’s hyper-connected world, organizations face a growing number of threats that extend far beyond their traditional network boundaries. Cybercriminals no longer limit themselves to direct system intrusions — they target your brand, employees, customers,…
Is Cybersecurity Hard? A Beginner’s Guide to Get Started
For many beginners, the idea of pursuing a career or even just learning about cybersecurity can feel intimidating. The term itself conjures images of hackers, firewalls, and complex code. It’s no surprise that one of…