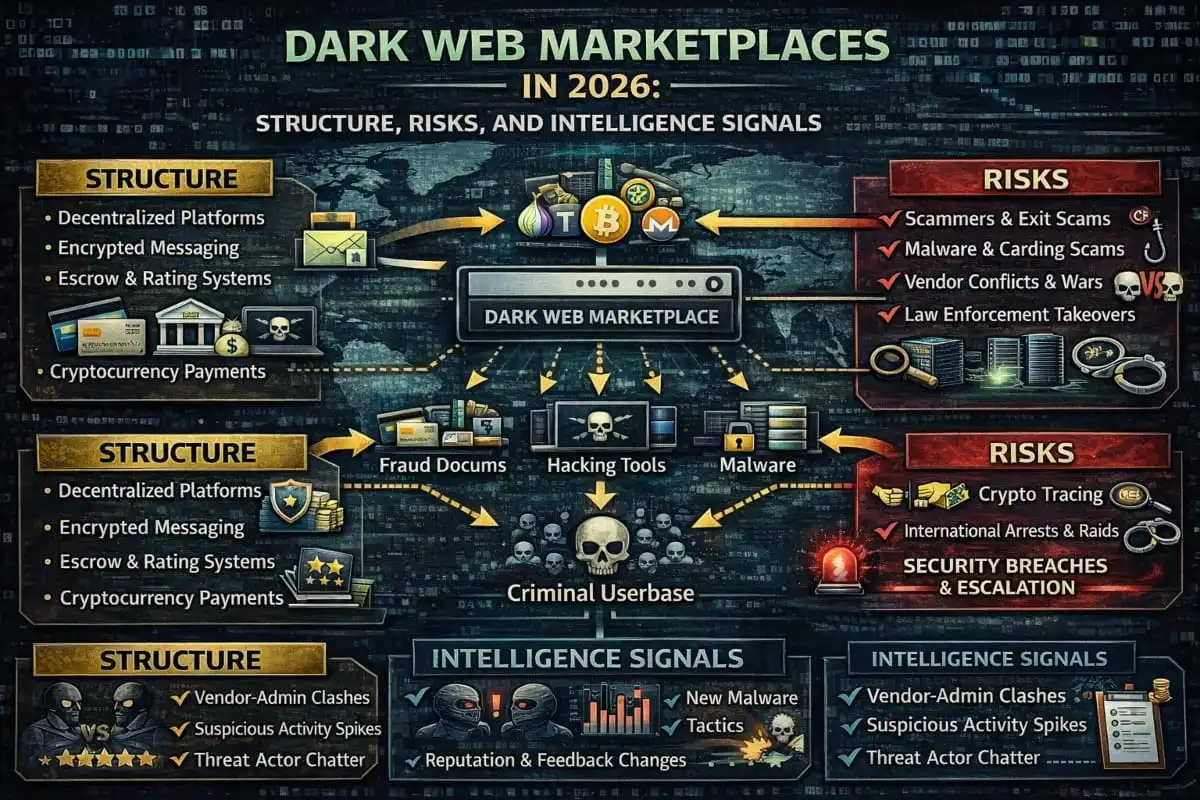
Despite major law enforcement takedowns, the dark web ecosystem remains active in 2026. A small number of dominant marketplaces continue to facilitate illicit trade, adapting quickly to seizures, arrests, and infrastructure shutdowns.
Current Landscape
As of 2026, seven marketplaces account for much of the activity across drugs, stolen data, and digital crime services:
- Abacus Market and TorZon Market operate as multi-purpose hubs that offer drugs, compromised data, and digital goods to a global user base.
- STYX Market specializes in financial fraud services.
- Brian’s Club focuses on stolen credit cards and payment data.
- Russian Market and BidenCash (until its mid-2026 takedown) concentrate on breached credentials and stealer logs.
- WeTheNorth serves as a regional marketplace primarily targeting Canada.
These platforms function much like significant e-commerce marketplaces, enabling anonymous transactions across multiple illicit categories.
How These Markets Operate
Dark web marketplaces typically run as hidden services on the Tor network and rely on cryptocurrency payments, most commonly Bitcoin and Monero. Standard operational features include escrow systems, invite-only access, reputation scoring, and encryption. However, many markets still collapse due to exit scams or coordinated law enforcement action.
History of Dark Web Marketplaces
Dark web marketplaces entered the mainstream with Silk Road, launched in 2011. It popularized the idea of anonymous online marketplaces operating over Tor, using Bitcoin for payments. That visibility brought intense scrutiny, and the marketplace was ultimately shut down by the FBI in 2013.
After Silk Road, the ecosystem shifted into a cycle of rapid growth and disruption. Markets like AlphaBay, Hansa, and Dream Market rose to fill the gap, only to later be seized, dismantled, or abandoned. Some were taken down through coordinated law enforcement operations, while others disappeared suddenly, often due to exit scams, internal disputes, or security failures.
Over time, the pattern has remained consistent. Each new wave of marketplaces seeks to improve operational security and trust mechanisms (such as escrow and vendor reputation), while defenders and authorities adapt their tactics in response. The result is an environment defined less by “permanent top markets” and more by constant churn, rebrands, and migration across platforms and channels.
Why Activity Remains High
Despite crackdowns, usage of Tor and dark web services remains substantial. In recent years, the network has averaged millions of daily users globally, with usage patterns shifting by region as enforcement pressure changes.
This persistence matters because darknet markets remain a critical supply chain for cybercrime. Data sold today can enable future account takeovers, financial fraud, and ransomware attacks. Even low-cost purchases, such as those made with stolen payment cards, can result in significant downstream harm.
Why This Matters in 2026
The dark web’s underground economy has direct real-world consequences. Organizations now routinely conduct dark web exposure assessments to determine whether customer data, employee credentials, or internal access points are being traded.
Security teams increasingly rely on dark web monitoring and threat intelligence to detect early indicators of compromise. At the same time, ongoing takedowns create constant volatility, making it essential to understand which marketplaces are active and what types of data they handle.
Staying informed about the structure and evolution of dark web markets is now a core requirement for cybersecurity, risk management, and fraud prevention in 2026.
Tracking these marketplaces isn’t about “browsing the dark web”; it supports dark web monitoring, threat intelligence, and data exposure assessments. When carding brands are seized (e.g., BidenCash) or large markets go dark (e.g., Abacus), actors migrate, listings repost, and stolen datasets resurface elsewhere, which is precisely why organizations need continuous monitoring and response workflows, not one-time checks.
Abacus Market
Abacus Market launched in 2021 and rose to become the dominant English-language darknet marketplace after earlier major platforms collapsed. By 2024, it was widely described as the leading Western Market for activity and visibility, effectively functioning as a “one-stop” illicit marketplace for a broad range of contraband categories.

Abacus operated as a multi-category marketplace, with listings spanning:
- Illegal drugs and unlicensed pharmaceuticals
- Counterfeit/forged documents
- Cybercrime-related goods (e.g., stolen financial data, compromised accounts, and other “crimeware” style listings)
Several threat-intel and reporting sources characterized it as having tens of thousands of listings and being one of the most essential Western-facing markets at its peak.
In 2024, multiple reports cited Abacus as holding a substantial share of Bitcoin-enabled activity on Western darknet marketplaces, often described at ~70% in that segment.
Like many darknet markets, Abacus was reported to rely on familiar marketplace mechanics such as:
- Escrow-style transaction handling
- Vendor reputation/feedback dynamics
- Crypto payment rails (often referenced in reporting and threat intel coverage)
These traits are frequently cited as reasons why such markets can scale quickly and why failures can cause widespread losses for participants.
Abacus 2026 Status
In early to mid-July 2025, Abacus went offline amid widespread reporting and industry assessment of a likely exit scam (operators disappearing with funds held in escrow). However, some coverage noted that the possibility of covert law enforcement action could not be entirely ruled out at the time. In practical terms, for defenders in 2026, Abacus is treated as a collapsed/offline market whose disappearance contributed to further fragmentation and migration across the ecosystem.
Why the Abacus still matters for security teams in 2026
Even after a market collapses, the “blast radius” can persist:
- Vendor and buyer migration to other venues
- Re-listing of previously sold or recycled stolen data
- Increased chatter, impersonation, and scam activity during “market vacuum” periods
For organizations, this reinforces why dark web monitoring and exposure assessments focus on signals and movement, not just on a single Market’s existence.
STYX Market
STYX Market is widely described in threat intelligence reports as a specialized cybercrime marketplace that emerged in early 2023 and gained attention following the disruption of major “fraud-access” ecosystems such as Genesis Market.

Unlike broad, drug-heavy darknet markets, STYX is characterized as fraud-centric, with listings commonly associated with:
- Stolen financial data (payment card data, account access, identity datasets)
- Compromised access and “logs” (often discussed as stealer-log style data and remote-access credentials)
- Fraud enablement services (e.g., cash-out / laundering-type services advertised in underground commerce contexts)
This positioning is a key reason it’s frequently discussed as a financial-crime hub rather than a general contraband bazaar.
Multiple sources frame STYX as part of a broader pattern. When a central marketplace is disrupted, demand migrates to newer venues that specialize and add stronger trust/controls to attract “serious” buyers and sellers. The Genesis Market takedown in 2023 is often cited as one catalyst that reshaped the fraud marketplace landscape.
Reporting commonly highlights features designed to increase transaction confidence in illicit environments, such as:
- Escrow-style brokering
- Vendor trust/verification signals
- Off-platform comms/announcement channels (often Telegram mentioned in coverage)
These features matter to defenders because they correlate with repeatable supply chains (where the same types of stolen data and access can be sourced at scale).
STYX 2026 Status
There is no widely documented, authoritative public takedown notice in the sources above tying STYX to a confirmed seizure/arrest operation, and recent industry posts continue to discuss it as a relevant marketplace in the fraud ecosystem. That said, the “STYX” name is also used by multiple public-facing domains and lookalikes, so analysts often caution against assuming any single website equals the original operation.
Why it matters for organizations in 2026
markets like STYX are closely associated with the trade of data and access that can enable account takeover, business email compromise, fraud, and initial access to ransomware, making them relevant to dark web monitoring, exposure assessments, and threat intel prioritization.
Brian’s Club
Brian’s Club (often styled as BriansClub / Brian’sClub / BrianCC) is a long-running carding marketplace that has operated since the mid-2010s and is best known for selling stolen payment card data. Its branding is widely described as a taunt aimed at journalist Brian Krebs, whose reporting has chronicled carding ecosystems for years.

Brian’s Club is primarily associated with the sale of:
- Stolen card data used for payment fraud (e.g., “dumps”/track-style data and card-not-present data bundles)
- Identity-linked financial datasets are sometimes packaged for impersonation and account fraud
Unlike multi-vendor “everything markets,” it’s often described as a specialized store focused on payment-card fraud supply chains.
In 2019, a large cache of data associated with Brian’s Club was leaked and shared with financial institutions, enabling banks to identify and replace exposed cards. Krebs’ reporting and follow-up analysis commonly cite tens of millions of card records tied to the incident, accumulated over several years.
Brian’s Club 2026 Status
Public reporting around “is it shut down?” remains noisy: there have been repeated claims of disruptions or shutdowns, alongside indications of mirrors/continuations/rebrands that keep the name circulating. The most defensible way to describe it in 2026 is that the “Brian’s Club” ecosystem persists in some form. Still, precise operational status is difficult to verify from open sources because of copycats, mirrors, and churn.
Why it matters for defenders in 2026
Carding shops like Brian’s Club are essential to monitoring programs because they signal:
- Payment card exposure (often tied to skimmers, POS compromises, or third-party breaches)
- Fraud risk escalation windows (when newly posted data tends to be most actionable)
- Downstream identity and account takeover risk when card data is bundled with identity attributes
That’s why many organizations treat this category as a core input to dark web exposure assessments and fraud/threat intelligence.
WeTheNorth Market
WeTheNorth (WTN) emerged in 2021 as a regionally branded darknet marketplace with a strong Canadian identity. Unlike large “global” markets, WTN built traction by targeting local preferences and cultivating a community-first reputation, including bilingual positioning (English/French) and a vendor base associated with Canada.

As reported in ecosystem discussions, WTN has been linked to multi-category illicit listings, often with a regional emphasis:
- Controlled substances and regulated products (commonly described as a primary category for the Market).
- Counterfeit and identity fraud materials, including documents and supporting artifacts, are often aligned with Canadian contexts.
- Financial fraud–related items, including compromised payment data and related tooling (generally viewed as smaller in scale than specialist platforms).
- Cybercrime-adjacent goods and services, including malware/tooling and “hire services” offerings.
- Digital guides/tutorial content that can indicate a “training” layer for lower-skilled actors.
For defenders, the most crucial point is that markets like WTN can act as local distribution nodes for fraud enablers and compromised data, especially when they prioritize regional “trust” and repeat transactions.
WTN is frequently described as emphasizing trust and moderation compared to larger, higher-chaos markets. In practice, markets that push “community rules” and vetting can:
- Reduce open scamming (increasing buyer confidence and repeat purchasing)
- Improve vendor stability (making supply more predictable)
- Increase the likelihood that stolen data and fraudulent goods circulate longer within a smaller, loyal audience
WTN has also been described as prohibiting specific high-heat categories (e.g., weapons, explosives, extremist content, child exploitation). Whether due to ethics or risk avoidance, such restrictions often serve as law-enforcement risk management and brand positioning, rather than reducing overall harm.
WTN is generally portrayed as mid-sized relative to global giants, but meaningful within Canada-focused trade. A steady-growth model (rather than explosive expansion) can be a survival strategy: smaller markets may attract less immediate disruption while still generating consistent illicit activity.
WeTheNorth 2026 Status
By late 2025, WTN is commonly characterized as still operating and comparatively stable (with periodic disruption risks typical of the ecosystem). For defenders, “stability” increases relevance: stable markets are more likely to show recurring patterns of data resale and repeat-vendor behavior, which can be monitored for exposure signals.
Why it matters for organizations
WTN is relevant in 2025 because regional markets can be a source of:
- Credential exposure and account takeover risk (employee/customer accounts)
- Identity fraud and synthetic identity creation (especially where local documents are emphasized)
- Payment fraud enables (stolen card data, bank-access artifacts)
- Early signals of compromise when datasets referencing a company, domain, or customer base appear
Defensive implication: treat WTN as an exposure-and-fraud signal source in threat intelligence workflows, especially for organizations with Canadian customers, operations, or employee populations.
TorZon Market
TorZon (often stylized TorZon/Torzon) is a multi-category darknet marketplace that emerged in 2022 and gained visibility as larger markets faced seizures, instability, or closures. By 2025, it is frequently discussed as one of the prominent English-language marketplaces in the broader ecosystem.

TorZon is commonly described as a generalist marketplace rather than a niche platform, with listings spanning multiple illicit categories. In threat-intel terms, the categories that matter most for organizational risk include:
- Stolen data and compromised accounts (credentials, payment-related data, and related datasets)
- Cybercrime tooling and services (malware, exploitation tooling, and other enablement content)
- Fraud-related goods (counterfeits, identity fraud materials, and adjacent services)
While controlled substances are often cited as a significant part of generalist markets, the most direct business impact typically comes from credential exposure, payment fraud enablement, and stealer-log distribution.
TorZon’s rise is often attributed to timing and continuity: when competing platforms shut down or lost user trust, displaced vendors and buyers migrated to surviving options. Markets that avoid major trust failures early can rapidly accumulate listings and become “default destinations” in community discussions, an essential signal for defenders because it suggests:
- More data resale velocity (fresh breaches and logs move faster)
- More vendor consolidation (repeat sellers reappear across markets)
- Higher signal value for exposure monitoring (brand/domain mentions, targeted sectors, etc.)
Ecosystem commentary often highlights “trust features” intended to reduce scams and impersonation risks within the Market itself. From a defensive lens, these features matter because they can increase the reliability of illicit commerce, which increases downstream harm.
Commonly discussed trust patterns include:
- Vendor reputation mechanisms that reduce buyer uncertainty
- Stronger verification norms to counter phishing and impersonation
- Support for privacy-preserving payment options (often discussed as an ecosystem trend)
You don’t need to explain mechanics; the key message is: more trust = more repeat transactions = more sustainable criminal supply chains.
TorZon Market 2026 status
As of late 2025 (per community reporting), TorZon is often described as active and prominent, meaning it may be relevant to:
- Exposure assessments (customer/employee credentials, internal access hints)
- Fraud risk monitoring (payment data resale, account takeover enablement)
- Threat actor tradecraft tracking (which tool families and log types circulate)
Large, stable markets also tend to become priority targets over time, making their status volatile. For defenders, volatility itself is a signal: disruption events often trigger migration waves, which can temporarily spike data reposting, rebranding, and scam activity elsewhere.
TorZon is often portrayed as a marketplace that adopted trust-building design choices earlier than many newer entrants, helping it onboard established vendors and accelerate perceived legitimacy. This “fast maturity” pattern is essential for threat intelligence because it can rapidly shift where the highest-value datasets and vendors concentrate.
Russian Market
Russian Market is a long-running illicit data marketplace (active since roughly 2019) that caters to a global audience and is widely referenced in cybersecurity reporting for trafficking in compromised digital assets. In 2026, it’s best understood as a data-centric marketplace rather than a “general contraband” market; its primary role is enabling credential abuse, account takeover, and fraud supply chains.

From a defensive lens, the Russian Market is most strongly associated with:
- Compromised credentials and accounts (email, consumer platforms, enterprise access paths)
- Remote access exposure (e.g., stolen/abused access to systems that can enable deeper intrusion)
- Stealer-log ecosystems (credential/cookie/session artifacts harvested by information-stealing malware)
- Payment and identity fraud data (card-related datasets and identity attributes used for fraud and social engineering)
- “Enablement” content that reduces friction for fraud workflows (the key point is the enablement, not the mechanics)
Exact size is hard to verify publicly, but the Russian Market is consistently discussed as a high-volume, high-churn venue where new datasets and access artifacts appear frequently. In 2026, that “freshness” is one of the reasons it remains relevant to defenders, markets with rapid turnover tend to be early indicators of new campaigns and newly circulating breach material.
Russian Market’s “security posture” is best described as anti-observation and anti-scraping, not “secure” in any legitimate sense. Data markets typically implement friction designed to limit casual visibility and automated collection while preserving a smooth experience for paying users. For defenders, the important takeaway is that these design choices can make stolen-data trafficking more sustainable and repeatable, which increases downstream risk.
Russian Market Status (2026)
In 2026, the Russian Market should be treated as a continuing exposure and fraud signal source (i.e., relevant for monitoring and assessment). Because marketplace status can change quickly (seizures, exit events, rebrands, disruption), the safest language for 2026 is to describe it as actively referenced and monitored rather than making absolute uptime claims.
Russian Market matters in 2026 because it directly supports the most common high-impact attack paths:
- Account takeover via credentials, sessions, and stealer-derived artifacts
- Initial access that can lead to business email compromise, internal system abuse, or ransomware staging
- Fraud at scale using payment and identity datasets
- Exposure assessment for brands: employee/customer credentials and domain-linked artifacts can appear soon after compromise
Defensive implication: If you conduct dark web exposure assessments in 2026, prioritize detection for credentials, stealer logs, and access artifacts; these typically result in the fastest real-world incidents.
BidenCash
BidenCash was a carding-focused cybercrime marketplace launched in March 2022 and became widely known for pairing sales of stolen payment data with attention-grabbing “free dump” promotions. In June 2025, U.S. authorities announced the seizure of infrastructure tied to the marketplace, disrupting its operations.

From a defender’s perspective, BidenCash primarily enabled:
- Stolen payment card data and associated personal information were used for fraud.
- Compromised credentials that could be used to access systems “without authorization,” as described in the U.S. seizure announcement.
- “Promotion dumps” of stolen card data were publicly released on the Market platform (as documented by multiple security reports).
Law enforcement stated the marketplace:
- Supported 117,000+ customers
- Facilitated trafficking of 15+ million payment card numbers
- Generated $17+ million in criminal revenue (transaction fees)
BidenCash’s “security” was less about protecting users and more about staying online and reducing friction for repeat fraud. The same seizure announcement notes that authorities took action against both darknet and traditional internet domains, indicating that the marketplace relied on a broad domain footprint rather than a single, stable presence.
Its promotional leaks, while effective marketing, also increased visibility and likely elevated enforcement priority.
BidenCash Status (2026)
Inactive/disrupted. In June 2025, U.S. authorities announced they seized ~145 domains and associated cryptocurrency tied to BidenCash, effectively dismantling its public-facing infrastructure.
BidenCash is a 2026 case study in how high-velocity payment fraud ecosystems operate:
- Large-scale carding marketplaces can rapidly amplify card-not-present fraud, identity misuse, and downstream account abuse.
- Public “free dumps” can prompt rapid defensive measures (re-issuance, monitoring spikes) and broaden the impact on victims beyond typical underground buyers.
- Even when a central platform is seized, activity tends to migrate, so monitoring should focus on signals of exposure and reposting rather than assuming demand disappears.
Mellow (Voluntary exit April 2023)
Mellow was a short-lived darknet marketplace that operated from late 2022 into 2023 before shutting down via a voluntary exit. EUDA’s darknet market closure dataset lists Mellow as starting 01 September 2022 and ending 25 April 2023, with the closure reason recorded as Voluntary exit.
As a general-market style platform (typical of many DNMs at the time), Mellow was associated with common illicit marketplace categories (e.g., controlled substances and other contraband). For defensive coverage in 2026, the key point is not the specifics of the catalog, but that Mellow followed the standard DNM pattern of enabling anonymized trade and associated fraud/cybercrime spillover.
Compared to long-running “giant” markets, Mellow’s footprint was limited by its short lifecycle (under a year). Public reporting on DNMs routinely describes the ecosystem as relying on trust mechanisms (reputation, escrow-like controls, and anti-scam signaling) to sustain activity, while remaining vulnerable to trust failures, coercion, and abrupt closures.
Inactive. As of 2026, Mellow is best treated as a closed market that exited in April 2023, not an active venue. Mellow is a valuable case study of market churn: new DNMs can appear credible, attract activity, and then disappear quickly. For defenders, the lesson is to monitor signals and migrations (where vendors/data move next) and to treat darknet exposure as an evolving supply chain rather than a static list of “top markets.”
Omicron (Hacked, July 2022)
Omicron was a short-lived darknet marketplace that operated in 2022 and was reported to have been hacked in July of that year. The EUDA (European Union Drugs Agency) dataset lists Omicron with a start date of 30/03/2022 and an end date of 23/07/2022, with the closure reason marked Hacked.
As with many general darknet marketplaces tracked in this period, Omicron is best understood (from a defender’s perspective) as part of the broader illicit-market ecosystem, where contraband trade and cybercrime-adjacent activity can overlap, especially around fraud, compromised accounts, and data-exposure signals.
Omicron’s lifecycle was very short (roughly four months), which typically limits long-term market depth and stability compared to major, multi-year markets. Its “hacked” classification of closure is a valuable reminder that marketplace operators and users face persistent compromise risk (platform vulnerabilities, insider risk, and operational failures). For defenders, this volatility often triggers migration of vendors/data to other venues and can temporarily increase reposting of datasets elsewhere.
Inactive. Omicron is recorded as ending on 23 July 2022 due to being hacked, so it should not be treated as an active marketplace in 2026. Omicron matters mainly as a market-churn case study: hacks and sudden shutdowns don’t end the underlying activity; they redistribute it. For 2026 monitoring, the practical takeaway is to track where communities and datasets move after disruptions, and to treat “market lists” as dynamic rather than static.
AlphaBay ( Dec 2022)
AlphaBay was one of the most significant darknet marketplaces of the 2010s. The original AlphaBay is recorded as operating from 22 December 2014 → 28 June 2017 and ending due to a law-enforcement takedown (“Raided”), not an exit scam.
A separate relaunch attempt was publicly discussed in 2021, attributed to a former administrator (“DeSnake”), and tracked by multiple threat-intel/commentary sources as a “return.”
During the 2017-era takedown, authorities described AlphaBay as facilitating sales of illegal drugs, malware, counterfeit identification documents, and other illegal services. (For a 2026 defensive write-up, this is enough; no access or operational detail is needed.)
AlphaBay was widely characterized as a significant global marketplace before its 2017 takedown, and Europol described the 20 July 2017 operation as targeting “two of the largest” markets (AlphaBay and Hansa).
The AlphaBay/Hansa operation is often cited as a reminder that “marketplace security” is fragile: enforcement can seize infrastructure and gather user data through coordinated, cross-border investigations.
The 2021-era “AlphaBay return” discussions also emphasized upgraded security claims (e.g., stronger operational security and a safer payment posture). However, these were claims made by operators/observers rather than independently verifiable guarantees.
Inactive/defunct as a reliable market brand. The original AlphaBay ended with the 2017 raid. Separately, “AlphaBay’s return” (2021) is best treated in 2026 as unstable and historically volatile, not a dependable “active market” reference point.
AlphaBay matters less as an “active venue” and more as a template for how the ecosystem behaves: takedowns don’t remove demand, they trigger migration, rebranding, and rapid vendor relocation. That churn is precisely why modern programs focus on exposure monitoring and early warning signals (credentials, stealer logs, fraud enablement) rather than chasing static “top market” lists.
World Market (Exit scam, March 2022)
World Market was a darknet marketplace that operated from 09 November 2020 until 08 March 2022, when it was classified as an exit scam (operators disappearing with funds).
As a mainstream “multi-category” market of its era, World Market fit the broader darknet market pattern, in which illicit listings commonly include drugs and other contraband, alongside fraud- and cybercrime-adjacent activity that can spill into credential abuse and financial crime.
Specific verified user/vendor counts are difficult to validate publicly. Still, its ~16-month lifespan indicates it was more established than many short-lived markets, long enough to build repeat vendor/buyer activity before collapsing.
The key security takeaway is structural: exit scams are a recurring failure mode in darknet markets, reflecting fragile trust, centralized control points, and persistent pressure from fraud, disruption, and enforcement dynamics across the ecosystem.
Inactive. World Market is recorded as ending on 08 March 2022 due to an exit scam, so it should not be treated as active in 2026.
World Market is useful as a 2026 case study in market churn: when a market collapses (exit scam vs. takedown), the underlying activity typically migrates, vendors re-list elsewhere, and stolen data/fraud goods can be reposted across new venues. That’s why modern defenders prioritize continuous monitoring and exposure assessment over static “top market” lists.
Kingdom Market (Raided, December 2023)
Kingdom Market was an English-language darknet marketplace that operated from at least April 2021 until it was taken down in December 2023. The EUDA dataset records Kingdom Market: 19/04/2021 → 19/12/2023 (Raided).
Authorities and reporting tied Kingdom Market primarily to narcotics, with additional illicit categories commonly seen on multi-purpose markets (e.g., malware/hacking tools and forged IDs).
Publicly verifiable scale metrics (users, listings, revenue) are limited. Still, its multi-year run placed it among the more established markets of its period, long enough to develop repeat vendor/buyer activity before disruption.
For 2026 defensive context, the key lesson isn’t the platform mechanics, it’s the pattern: larger, longer-running markets become higher-priority targets, and coordinated multi-agency operations can end them abruptly, triggering rapid vendor and data migration elsewhere.
Inactive. Kingdom Market is recorded as raided in December 2023, so it should not be treated as active in 2026.
Kingdom Market is a practical 2026 example of ecosystem churn: takedowns don’t eliminate demand, they redistribute it. After a raid, vendors and datasets typically reappear on other platforms, and reposting spikes can create fresh exposure and fraud risk signals for organizations monitoring credentials, stealer logs, and brand mentions.
Tor2door Market (Exit scam, September 2023)
Tor2door Market was a darknet marketplace tracked in the EUDA dataset from 03 July 2020 until 14 September 2023, with its closure recorded as an exit scam.
As a multi-vendor darknet market, Tor2door fits the common “general marketplace” pattern seen across the ecosystem (often spanning contraband plus fraud/cybercrime-adjacent offerings). For a 2026 defensive write-up, the key point is that such venues can serve as distribution points for compromised data, facilitate fraud, and support related illicit supply chains.
Public, verifiable scale metrics (exact users/listings/revenue) are limited; however, operating for over three years suggests Tor2door reached meaningful traction before its collapse, long enough to develop repeat vendor/buyer activity.
Its end state (exit scam) reflects a recurring structural risk in darknet markets: trust can fail abruptly, and “market stability” can disappear without warning, often leading to sudden community migration and reposting of goods/data elsewhere.
Inactive. Tor2door is recorded as ending on 14 September 2023 due to an exit scam, so it should not be treated as an active marketplace in 2026.
Tor2door is a proper 2026 case study in ecosystem churn: when a market exits, scammers, vendors, and datasets typically move rather than vanish. For defenders, the practical takeaway is to monitor for migration waves (new venues, rebranded vendor identities, and fresh reposting of stolen data) as part of ongoing exposure assessment and threat intelligence.
Aurora Market (Exit scam, May 2021)
Aurora Market was a darknet marketplace tracked from 02 November 2020 to 04 May 2021, with its closure reason recorded as an exit scam in the EUDA dataset.
Aurora Market fit the typical “general darknet market” pattern of its era, where listings commonly span contraband and fraud/cybercrime-adjacent categories. For a 2026 defensive write-up, the most relevant angle is that markets like this can contribute to credential exposure, fraud enablement, and downstream account takeover risk.
Publicly verifiable scale metrics are limited, but its roughly six-month lifespan suggests it was relatively short-lived compared to multi-year markets, consistent with the high churn rate reflected in the EUDA market-lifecycle data.
Aurora’s end state (an exit scam) illustrates a recurring ecosystem risk: even when markets tout “trust” or “security,” structural incentives and pressures often lead to abrupt failure. For defenders, these failures typically trigger vendor migration and the reposting of data across other venues.
Inactive. Aurora Market is recorded as ending on 04 May 2021 due to an exit scam, so it should not be treated as active in 2026.
Aurora Market is useful in 2026 as a case study in market churn and trust collapse: when a market exits, scams and the underlying activity rarely disappear; they relocate. That’s why modern programs emphasize continuous dark web monitoring, exposure assessment, and migration tracking rather than static “top markets” lists.
ToRReZ Market ( December 2021)
ToRReZ Market was a darknet marketplace active from 28 February 2020 until 17 December 2021, when it voluntarily shut down. The operator announcement and reporting at the time framed the shutdown as a deliberate closure rather than an exit scam.
As a general darknet market, ToRReZ followed the typical multi-category pattern seen across the ecosystem (often including drugs and other contraband, alongside fraud- and cybercrime-adjacent offerings). For 2026 defensive coverage, the key relevance is its role as a venue where illicit supply chains and data/fraud ecosystems can overlap.
Contemporary reporting described ToRReZ as one of the larger markets at the time of its shutdown (including claims of being among the “second largest” by listings in late 2021).
The most critical “security” lesson is structural: even when a market appears stable, it can still disappear quickly due to operator decisions. That sudden shutdown dynamic creates migration waves (vendors and datasets moving elsewhere), which is often more important for defenders than the Market’s internal mechanics.
Inactive. ToRReZ is recorded as ending on 17 December 2021 via voluntary exit, so it should not be treated as active in 2026.
ToRReZ is a practical 2026 example of market churn without law-enforcement seizure: voluntary closures still redistribute activity across other venues. For monitoring programs, the takeaway is to track post-closure migration and reposting of compromised data/fraud listings rather than relying on static “top market” lists.
Genesis (Exit scam, August 2019)
Genesis was a darknet marketplace tracked by the EUDA dataset from 01 May 2019 until 24 August 2019, ending as an exit scam.
The EUDA dataset categorizes entries as darknet markets offering drugs, so Genesis should be treated (in a 2026 write-up) as part of the drug-market ecosystem that can also overlap with fraud and other illicit trade patterns.
Genesis had a short lifecycle (under 4 months), which typically limits long-term depth and stability compared with multi-year markets.
Its closure type, exit scam, highlights a recurring ecosystem failure mode: markets can collapse without warning due to operator misconduct, triggering sudden loss of trust and rapid migration elsewhere.
Inactive. Genesis is recorded as ending on 24 August 2019 due to an exit scam, so it is not active in 2026.
Genesis is a helpful example of market churn in 2026: when an exit scam occurs, activity doesn’t vanish; it relocates, often causing short-term spikes in re-listing, reposting, and fragmentation across other venues, which are relevant for exposure assessment and threat-intel tracking.
Dark Web Marketplace Trends in 2026
1) Consolidation after significant disruptions
The ecosystem keeps shrinking and reshaping around fewer “survivor” markets after major takedowns and shutdowns. The 2025 dismantling of Archetyp Market is a good example of how a single operation can force rapid vendor/buyer migration and reshuffle the leaderboard.
2) More exit risk than ever
In 2026, operator trust is still the weakest link. Large markets keep disappearing via likely exit scams, often right after ecosystem turbulence increases user inflows and wallet balances. TRM Labs’ assessment of Abacus going offline as a possible exit scam illustrates this pattern.
3) Data markets keep growing because they monetize cybercrime directly
Marketplaces focused on credentials, stealer logs, and access remain central because they map cleanly to account takeover, fraud, and ransomware staging. This is why BidenCash mattered: it industrialized carding at scale until its 2025 infrastructure seizure.
4) Infrastructure “sprawl” and rapid rebranding
A clear 2026 trend is many domains/entry points, with fast rotation, to withstand disruption. The BidenCash case is a concrete data point: the U.S. announced seizure of ~145 domains tied to the marketplace.
5) Cross-border enforcement is increasingly coordinated
Instead of single-country actions, the pattern is multi-country, multi-agency operations aimed at administrators, top vendors, and infrastructure. Europol’s Archetyp operation highlights this approach.
Related enforcement campaigns also target broader drug networks and darknet-linked supply chains (e.g., Operation RapTOR announcements).
6) Crypto remains the payment rail, but tracing pressure rises
Markets still rely on cryptocurrency, but enforcement and blockchain intelligence pressure continuecontinue to increase, which contributes to shorter market lifecycles and more sudden exits (scams or seizures). The DOJ statements around seizures (domains + crypto) reinforce that this is a core disruption lever in 2026.
7) What defenders should prioritize in 2026
If your goal is monitoring and exposure assessment (Dexpose-style positioning), the highest-signal trends are:
- Stealer-log + credential circulation (fastest path to ATO and initial access)
- Market migration waves after a seizure/exit (reposting spikes and new “brand” emergence)
- Domain/infrastructure churn (many domains, short-lived mirrors, frequent impersonation)
How Dark Web Marketplaces Operate in 2026
In 2026, dark web marketplaces function as semi-structured criminal platforms rather than anonymous forums. Most rely on escrow systems to manage transactions, vendor reputation scores to establish trust, and layered operational security to reduce exposure. Payments increasingly favor privacy-focused cryptocurrencies, while multisignature wallets help limit direct theft by marketplace operators.
A key shift is the decentralization of activity. Marketplaces are no longer the sole hub for communication. Vendors and administrators routinely use Telegram for announcements, dispute handling, and migration during outages or takedowns. This hybrid model reduces reliance on any single platform and makes the ecosystem more resilient to disruption.
Dark Web Marketplaces in 2026: Structure, Risks, and Intelligence Signals
The internal structure of most marketplaces is built around categories such as digital fraud, stolen credentials, access brokerage, and illicit services. While the surface structure appears organized, underlying risks are high for both users and operators.
From an intelligence perspective, marketplaces generate valuable signals before threats become visible elsewhere. Early indicators often include sample data releases, changes in vendor behavior, sudden increases in specific listing types, or discussions about breached organizations. These signals frequently precede phishing campaigns, account takeovers, or ransomware activity observed on the open web.
What to Monitor Instead of Visiting Marketplaces
Effective monitoring does not require direct access to the marketplace. More actionable intelligence comes from observing surrounding activity across forums, chat platforms, and leak channels. This includes discussions referencing new data breaches, credential samples posted as proof, and migration announcements when marketplaces experience disruption.
Tracking patterns, such as repeated mentions of a company name, reused wallet addresses, or consistent vendor aliases, helps validate threats and assess risk without unnecessary exposure. Correlating these signals across Tor-based forums and Telegram channels provides a clearer picture of emerging threats than marketplace visibility alone.
How Dexpose Approaches Dark Web Marketplace Intelligence
Dexpose approaches dark web marketplace intelligence with a focus on monitoring and analysis rather than direct browsing. Instead of accessing marketplaces, Dexpose tracks activity across relevant Tor-based forums and associated Telegram channels to identify risk signals tied to fraud, data exposure, and emerging criminal campaigns.
By correlating signals across multiple surfaces, such as marketplace-related discussions, leak announcements, and off-platform coordination, Dexpose helps security teams detect threats earlier and with greater confidence. This cross-source correlation reduces false positives and provides context that single-channel monitoring often misses.
Dexpose also emphasizes early-warning alerts and evidence capture to support investigation and response. When indicators such as credential samples, brand impersonation, or access brokerage activity appear, security teams receive timely, actionable insights for validation, internal escalation, and remediation, without unnecessary exposure to illicit platforms.
Conclusion
Dark web marketplaces in 2026 are defined by instability, fragmentation, and constant change. While individual platforms come and go, the underlying threat patterns remain consistent. For defenders, understanding how these marketplaces operate and which signals matter is far more valuable than tracking rankings or attempting to access them.
Organizations concerned about data exposure, fraud, or credential abuse should prioritize monitoring, correlation, and response over visibility alone.