An Email security check is the first, smartest step toward protecting the messages, attachments, and account data that power both your personal life and your business. In a world where phishing lures, credential leaks, and automated scraping are routine, conducting an Email Security Check can quickly close the doors that attackers exploit. This guide walks you through a practical, professional, and prioritized plan that reduces risk, remediates exposure, and builds long-term resilience.
Why an Email Security Check Matters Now
Every inbox is a gateway. Compromised email accounts enable identity theft, account takeover, corporate espionage, and targeted social engineering. Performing an Email security check uncovers weak passwords, unreviewed third-party access, misconfigured forwarding rules, and leaked credentials the exact things attackers leverage to escalate privileges and harvest sensitive data.
Real world consequences
A single exposed credential can lead to months of silent data exfiltration. You may not notice unusual forwarding rules or subtle search-based filters that route copies of sensitive messages to an attacker-controlled account. Regular checks prevent minor mistakes from becoming catastrophic incidents.
What an effective email security audit looks like
This is a practical sequence for Data Leak Prevention you can follow today, whether you’re protecting a personal Gmail or a corporate Microsoft 365 tenant.

Step 1: Validate account credentials and access
- Confirm password strength and uniqueness for every account tied to your email address.
- Enforce long, unique passwords and consider a password manager for complexity and rotation.
- Revoke any unknown or unused devices from the account activity pages.
Enable multi-factor and authentication hardening
- Turn on two-factor authentication (2FA) using an authenticator app or hardware key.
- Prefer time-based one-time passwords (TOTP) or FIDO2 security keys over SMS.
- Check recovery options remove obsolete phone numbers or secondary emails.
Step 2: Scan for leaks and external exposure
- Use an Email breach checker to see if your address appears in public leaks and paste sites.
- Search for your email on search engines, public paste sites, and breach repositories to find accidental exposures.
- If you find a match, rotate passwords immediately and monitor for suspicious activity.
Investigating the broader fallout
If your address is part of a larger incident (for example, an Oracle data breach affecting enterprise credentials), treat that discovery as high-priority: notify your IT/security team, force password resets, and inspect privileged account usage logs.
Step 3: Review mail flow, forwarding, and rules
- Audit inbound/outbound forwarding configurations. Attackers often add invisible forwarders that copy mail to external accounts.
- Check for automated rules that archive, delete, or forward specific messages.
- Validate third-party app authorizations and OAuth tokens.
Control third party access (least privilege)
Remove or re-scope apps that request wide mailbox access. Replace legacy integrations with scoped API tokens and refresh grants regularly.
Step 4: Lock down attachments and links
- Train yourself and your organization to treat unexpected attachments and links as suspicious.
- Preview attachments in a sandbox or cloud viewer if available; avoid downloading unknown file types.
- Verify senders by an out-of-band method (e.g., separate chat or phone call) when requests are sensitive.
Step 5: Harden email transport and encryption
- Enforce TLS for email in transit and deploy SPF, DKIM, and DMARC records for your domains.
- Use end-to-end encryption for highly sensitive messages or attachments.
- For organizations, implement encryption gateways and key rotation policies.
Tools and advanced measures
From simple free checks to enterprise-grade integrations, here are tools and methods that genuinely reduce risk.
Lightweight checks for individuals
- Password manager: generate and store unique passwords.
- Built-in breach checks (Gmail, Microsoft, and many password managers offer this).
- Device activity pages: review and remove unfamiliar sessions.
Enterprise controls and monitoring
- Centralized logging and SIEM for email events.
- DMARC enforcement to prevent domain spoofing and phishing.
- Mail flow rules that flag or quarantine messages with high-risk indicators.
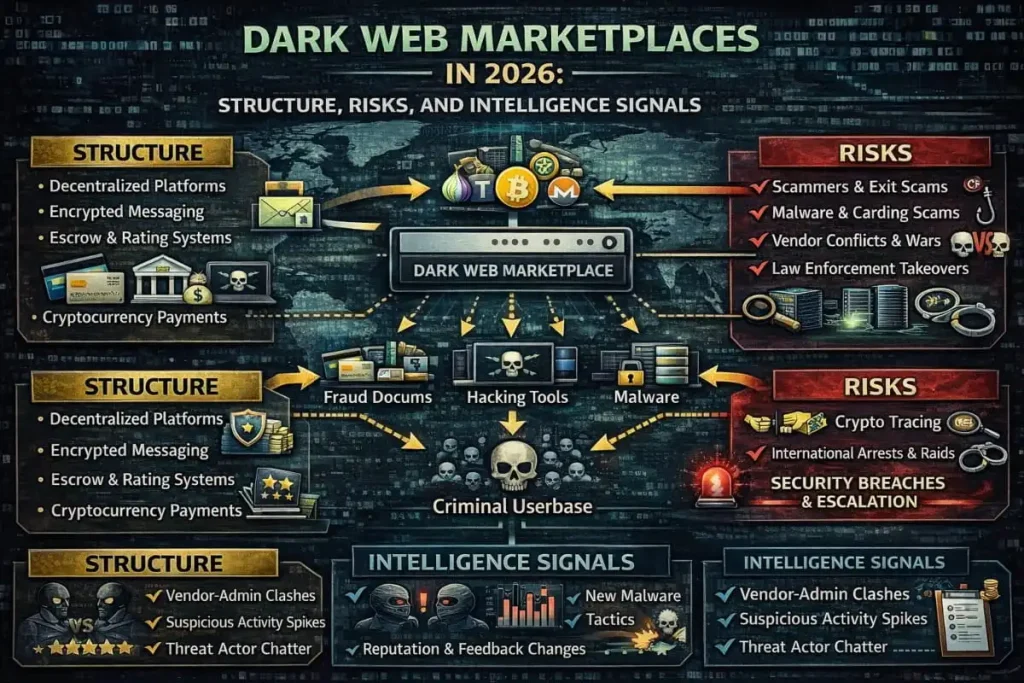
Threat intelligence and the dark web
Integrate monitoring to check if credentials or internal data appear on illicit marketplaces. Darkweb data API integration can automate alerts for leaked credentials tied to corporate domains and speed up incident response.
Humanc entered defenses: training, process, and culture
Technology alone isn’t enough. Build simple habits and workflows that reduce human error.
Train on phishing with context
Phishing simulations that mimic real-world tactics (voice, SMS, and social channels) are far more effective than sterile quizzes. dexpose teaches people how to verify requests for transfers, credential changes, or sensitive attachments.
Make incident reporting frictionless
A one click Report Phish button in the email client and a clear escalation path dramatically reduce dwell time for attackers.
Use Social Media Intelligence to spot targeted attacks
Monitor public social channels for signs of targeted reconnaissance; attackers often combine publicly available profile data with leaked credentials to craft persuasive social engineering. Social Media Intelligence helps you see the signals attackers use before they strike.
Technical deepdive: email authentication and protocols
This section explains the protocols that stop many automated attacks.
SPF, DKIM, and DMARC: how they work together
- SPF declares the IPs authorized to send mail for your domain.
- DKIM signs outgoing mail so recipients can verify the message integrity.
- DMARC ties SPF and DKIM results to a policy that prevents domain spoofing and reports abuse.
Implementing these reduces phishing and impersonation risks dramatically.
When to move from monitoring to enforcement
Start with a DMARC “none” policy to collect reports, then progress to “quarantine” and “reject” as you confirm legitimate senders are covered. Use aggregate and forensic reports to adjust settings.
Four everyday security habits (do these weekly)
- Check recent account activity and devices.
- Review third-party app access and revoke unnecessary permissions.
- Scan for your email address in breach databases.
- Verify domain DNS records (SPF/DKIM/DMARC) haven’t been altered.
Practical checklist for organizations (CISO-to-team handoff)
- Inventory all mailboxes and shared accounts.
- Enforce company-wide 2FA and password manager use.
- Set the DMARC policy to enforcement after testing.
- Integrate Brand Protection services to detect impersonation and typosquatting.
- Automate breach detection and response via API.
Note: Brand Protection here helps protect customers and employees from targeted phishing that spoofs your company identity it’s a powerful complement to mailbox hygiene.
Sample escalation flow (who does what)
- User reports suspicious email → Security triage.
- Triage confirms threat → Contain (deactivate account, revoke tokens).
- Investigate logs and scope impact → Notify affected parties.
- Remediate and recover → Reset credentials, clean devices.
- Post-incident review → Update controls and training.
How to measure success
- Reduction in successful phishing clicks (measurement from simulations).
- Percentage of accounts with enforced 2FA.
- Number of exposed credentials detected and remediated within 24 hours.
- DMARC compliant rate for outbound mail.
These KPIs shift your posture from reactive to proactive.
The role of automation and APIs
Automating detection and response shortens attacker dwell time. Leveraging Advanced Cyber Threat Intelligence, you can use automated workflows to disable accounts, revoke OAuth tokens, and trigger password resets when specific high-confidence indicators appear.”
When to integrate Darkweb and threat feeds
Connect a targeted feed or Darkweb data API integration to your incident response platform to enable automated containment actions when alerts about leaked credentials are generated. This reduces manual lookup and limits exposure windows.
Common pitfalls and how to avoid them
- Over-reliance on SMS 2FA choose authenticator apps or security keys.
- By ignoring forwarding rules, attackers create stealthy rules to siphon data.
- Neglecting third-party access unused integrations are attack vectors.
- Delayed breach response speed matters; automate where possible.
Sample email security policy (short version)
- All employees must use a company-approved password manager and MFA.
- OAuth approvals require security review and expiration terms.
- Any suspected compromise must be reported immediately via the security portal.
- Quarterly training and simulated phishing exercises are mandatory.
This kind of policy makes expectations clear and reduces friction in response.
Implementation timeline 90 day plan
- Days 1–14: Inventory, emergency password resets, and enable 2FA for high-risk accounts.
- Days 15–45: Deploy SPF/DKIM/DMARC, turn off legacy auth, start breach monitoring.
- Days 46–90: Integrate dark web feeds, deploy Brand Protection and Social Media Intelligence, conduct org-wide phishing exercise.
Quick wins you can do in 30 minutes.
- Run an Email breach checker for your address and reset any compromised passwords.
- Review active sessions and devices in your mail account and sign out of unfamiliar ones.
- Enable an authenticator app for MFA and remove SMS-based recovery numbers that are outdated.
4 concise, action-oriented email hardening tips

- Replace shared mailbox passwords with managed access and role-based permissions.
- Enforce strict OAuth scopes and audit refresh tokens monthly.
- Configure DMARC with reporting before enabling quarantine/reject.
- Use hardware security keys for administrators and privileged users.
Final checklist before you finish your email security check
- Passwords are unique + and in use.
- 2FA is enabled across accounts.
- No unknown forwarding rules or third-party tokens.
- DMARC/SPF/DKIM implemented and monitored.
- Active breach monitoring through an Email breach checker or equivalent feed.
Conclusion
An Email security check is more than a one-off task; it’s the foundation of a secure identity and information environment. By combining immediate hygiene steps, technical controls like DMARC and encryption, innovative use of threat intelligence, and culture-first training, you implement Digital Risk Protection, converting an inbox from a liability into a defended asset. Please start with the quick wins, schedule regular audits, and progressively adopt automation and monitoring to detect and neutralize risks before they turn into incidents.
Frequently Asked Questions
Q1: How often should I run an email security check?
Run a quick personal check monthly and a full audit quarterly; after any suspected breach, perform an immediate check and remediation.
Q2: Is 2FA really necessary for email?
Yes 2FA blocks most automated account takeovers and is critical for protecting recovery flows and sensitive communications.
Q3: Will DMARC stop all spoofing attempts?
DMARC dramatically reduces domain spoofing when enforced, but complementary controls (user training and filters) are still needed.
Q4: Should my business use dark web monitoring?
For organizations, automated monitoring indeed shortens response time when employee credentials or corporate data are exposed.
Q5: What’s the first thing to do if I find my email in a leak?
Immediately reset the password, revoke active sessions and tokens, enable MFA, and scan for unauthorized forwarding rules.