The term “oracle data breach” has become a focal point for IT leaders, security teams, and everyday users who depend on company systems to store sensitive information. In a single incident, an organization’s customer data, credentials, or proprietary records can be exposed, creating operational, legal, and reputational risks that ripple outward. This post explains what an Oracle data breach typically involves, why it matters to organizations of every size, and the practical steps you can take to detect, limit, and recover from exposure.
What an Oracle data breach means and who it affects
An Oracle data breach refers to unauthorized entrance, disclosure, or exfiltration of information stored in Oracle-managed systems, whether on-premises Oracle Databases, Oracle Cloud Infrastructure, or enterprise applications built on Oracle platforms. Because Oracle solutions are widely used by banks, retailers, management, and large enterprises, a breach can impact a diverse set of stakeholders: customers, partners, employees, and suppliers.
Why it matters
- Scale of exposure: Oracle systems often contain large, centralized datasets, and a single compromise can expose millions of records.
- Business continuity: Databases underpin marketing, processing, and operational systems; a breach may interrupt critical services.
- Regulatory and legal risk: Exposed personal data can trigger notification obligations and penalties under laws such as GDPR, CCPA, and other privacy regimes.
- Trust and reputation: Enterprises rely on trust; a shared breach undermines confidence and can cost more in the long term than the immediate response.
How breaches happen: common attack vectors
Understanding how attackers gain access helps design defense-in-depth controls. Below, we also emphasize how the best Dark Web Monitoring tools help detect these risks early by tracking the most common avenues of compromise.
1. Misconfiguration and excessive permissions
Misconfigured cloud resources, unsecured database endpoints, or overly permissive accounts give attackers a low-friction path to sensitive data.
2. Credential theft and weak authentication
Stolen or reused credentials, often harvested from phishing, malware, or third-party leaks, remain a top cause. Multi-factor authentication gaps increase risk.
3. Supply chain and third-party compromise
Vulnerabilities in third-party services or partners that integrate with Oracle systems can be exploited to pivot into a primary environment.
4. Exploited software vulnerabilities
Unpatched database engines or middleware may contain vulnerabilities that allow remote code execution or privilege escalation.
5. Insider threat and human error
Deliberate misuse or unexpected data sharing by staff can result in significant leakages, especially where data breach monitoring is weak or absent.
Signs and evidence of compromise
Detecting a breach early limits damage. Security groups should track technical and behavioral indicators.
Technical indicators
- Unusual outbound traffic patterns or large transfers to unknown destinations.
- Unexpected database queries, especially large SELECTs against sensitive tables.
- New or altered privileged accounts and changes to access control lists.
- Alerts from endpoint protection, SIEM, or network IDS tied to database hosts.
Behavioral indicators
- Spike in customer support calls regarding unauthorized access.
- Reports of leaked credentials appearing on public forums or marketplaces.
- Sudden changes in system performance or unexplained errors.
Detection and monitoring: approaches that work
A layered monitoring strategy increases detection speed and accuracy by combining internal telemetry, external threat intelligence, and an email breach checker.

Internal detection capabilities
- Real-time logging and retention of database audit logs.
- Anomaly detection is built into SIEMs to detect unusual queries and access patterns.
- Endpoint and server monitoring to detect lateral movement.
External visibility
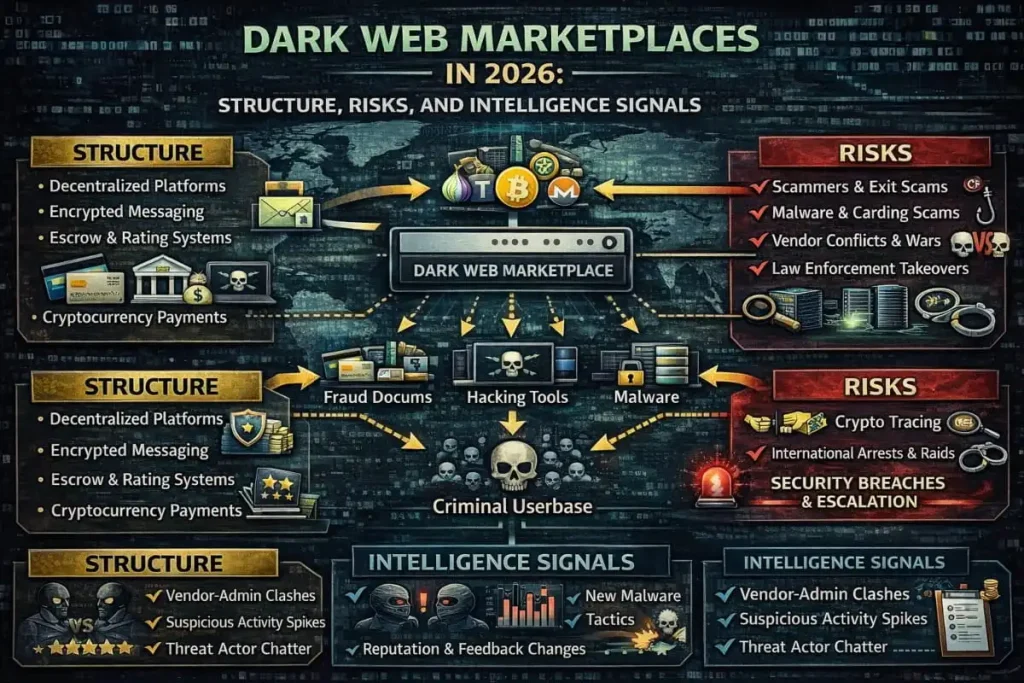
- Periodic Dark Web Monitoring to discover credential leaks or data listings.
- Subscribing to data breach monitoring feeds that correlate exposures to your domains.
- Running a free dark web scan or obtaining a Free Dark Web Report to check whether corporate assets appear in underground marketplaces.
Note: External tools complement internal detection; they rarely replace rigorous logging and alerting inside your surroundings.
Tools and services: choosing what to deploy
Selecting monitoring and detection tools depends on maturity, budget, and regulatory needs. Below is a concise comparison of categories and their purpose.
Comparison table: Monitoring and response tools
| Category | Purpose | Typical Outcome | When to use |
|---|---|---|---|
| Database Activity Monitoring | Records and analyzes SQL activity | Detects suspicious queries & privilege abuse | For high-value DBs with regulatory needs |
| Dark web intelligence | Scans underground marketplaces for leaked data | Early warning of credential and data leaks | When concerned about exposed credentials |
| Access governance | Enforces least privilege and tracks access | Reduces blast radius of stolen creds | In organizations with many privileged users |
| Cloud posture tools | Assess cloud config and permissions | Prevents misconfigurations | For cloud-first infrastructure |
| Incident response platforms | Orchestrates response workflows | Faster containment & reporting | When you need repeatable IR playbooks |
Practical detection checklist
- Enable and centralize database audit logs.
- Configure alerts for significant data exports or remarkable queries.
- Integrate Data Breach Detection signals into your SOC workflows.
- Schedule periodic deep- and dark-web monitoring scans to detect brand and credential exposure.
Incident response: a practical playbook
When evidence indicates a possible issue, an Oracle breach check ensures the sequence and clarity of actions determine how effectively you limit harm.
First 24–72 hours
- Contain isolated affected hosts or services to prevent further data exfiltration.
- Preserve evidence snapshot systems, capture logs, and register the chain of custody for forensic work.
- Assess scope, determine which databases, tables, or object stores were accessed, and what data types were affected.
- Communicate internally, notify leadership, legal, compliance, and PR teams, and activate your IR playbook.
Days 3–14: remediation and recovery
- Remove persistent access: revoke compromised credentials, rotate keys, and close exposed network paths.
- Patch and harden: apply updates, fix misconfigurations, and lessen unnecessary permissions.
- Notify stakeholders: fulfill regulatory notification requirements and inform affected users as applicable.
Weeks to months: post-incident improvements.
- Conduct a root-cause analysis and lessons-learned review.
- Implement compensating controls: stronger authentication, stricter segmentation, and automated detection.
- Evaluate whether Digital risk protection solutions should be added for ongoing external monitoring.
Practical containment actions
- Disable or isolate compromised service accounts.
- Block known exfiltration termini at the network level.
- Enforce immediate password and key rotations for high-risk identities.
Deepening detection: external scanning and email checks
Attackers frequently reuse credentials exposed in unrelated breaches to target enterprise systems. External scanning helps catch exposures you might miss internally.
- Use an Email breach checker or tools to check whether the email is compromised; these tools identify whether employee or admin email addresses have appeared in public leaks.
- Consider a dark web scan free as a baseline assessment; follow up with paid dark web monitoring services for continuous coverage.
- Evaluate the best Dark Web Monitoring tools by their coverage, speed, and ability to correlate leaks with your assets.
Brand protection and reputational monitoring
A data breach is as much a brand problem as a technical one. Monitoring for mentions of your company and leaked datasets is essential to managing your reputation and rapidly disproving false claims.
- Use Brand Protection tools to detect phishing pages using your logo or domain.
- Subscribe to Dark Web Insights feeds that alert you when company data shows up in marketplaces or forums.
Recovery and remediation: beyond patching
Fixing the immediate technical vulnerability is necessary but not sufficient. Effective recovery incorporates security improvements, policy change, and human-centered controls.
Access and identity hardening
- Enforce least privilege and implement just-in-time access for administrators.
- Require multi-factor authentication for database and cloud console access.
Data minimization and encryption
- Encrypt sensitive data at rest and in transit using proven cryptography.
- Remove unnecessary exposed columns from high-access tables, or tokenize them where possible.
Process and governance
- Update data retention and disposal policies to reduce the amount of sensitive data retained.
- Improve patch management and vulnerability scanning cadence.
Insurance, legal, and regulatory considerations
A breach triggers obligations and potential liabilities. Legal counsel and compliance teams should be part of every significant finding during the response.
- Assess notification timelines required by law and prepare compliant notices.
- Engage forensic and legal experts early to maintain privilege and prepare for potential litigation.
- Consider cyber insurance to offset breach response costs, and confirm whether your insurance covers cloud and third-party exposures.
Cultural and organizational measures
People and process matter as considerably as technology. Building a resilient organization involves training, simulated activities, clear lines of responsibility, and effective email detection.
- Conduct regular tabletop exercises simulating an Oracle data breach to align IT, legal, and communications.
- Run phishing-resistant training and measure behavior difference, not just completion.
- Assign a clearly identifiable incident commander and escalation matrix.
Quick-play action checklist
- Audit privileged accounts and enforce least privilege.
- Centralize logs and enable granular database auditing.
- Run a free dark web scan and consider paid dark web monitoring services for continuous coverage.
- Rotate credentials and keys after any confirmed exposure.
- Notify regulators and affected users promptly, in accordance with law and policy.
Common monitoring & detection concepts
- Data Breach Detection: Systems that identify signs of exfiltration or credential misuse.
- Breaches Monitoring: Constant tracking of new public and underground leaks against organizational assets.
- Deep and dark web monitoring: Searching hidden forums and marketplaces where stolen data is sold.
Three practical recommendations for executives
- Invest in detection and incident readiness. Faster detection lessens cost and harm.
- Prioritize identity protection credentials as the most common exploit path.
- Make external monitoring part of your baseline data leaks often surface outside your perimeter first.

Oracle security compromised
Short case-style scenarios
Scenario A: Misconfiguration leads to exposure
A misconfigured database endpoint permitted public reads—quick detection via monitoring, limited exposure to a subset of records. The organization patched the configuration, rotated keys, and issued regulatory notifications within required timeframes.
Scenario B: Stolen admin credentials
Check email data breach alerts helped reveal that admin credentials harvested from a phishing movement were utilized to query customer tables. Later, dark web intelligence showed those credentials for sale. The company deactivated the account, enforced MFA, and strengthened phishing defenses.
Table: Incident timeline example (quick view)
| Phase | Typical time | Key activity | Outcome |
|---|---|---|---|
| Detection | Minutes–day | Alerts from SIEM or external intelligence | Suspicion of compromise |
| Containment | Hours–2 days | Isolate systems, revoke access | Stop further exfiltration |
| Forensics | Days–weeks | Log analysis, snapshots | Determine scope & root cause |
| Notification | Days–weeks | Legal & regulatory actions | Fulfill obligations |
| Remediation | Weeks–months | Patch, harden, train | Prevent recurrence |
Measuring success: KPIs and metrics
- Mean time to detect (MTTD) and mean time to respond (MTTR).
- Number of exposed documents and time to notification.
- Reduction in successful phishing attempts after training.
- Coverage of external monitoring (percentage of critical assets monitored via Dark Web Monitoring.
Hiring and vendor selection tips
When selecting external partners for detection or brilliance:
- Demand concerns and case studies showing real-world detections.
- Verify the vendor’s data sources and how they correlate leaks to your assets.
- Confirm SLAs for detection, false-positive rates, and alert triage.
Practical advice for individual users
Not all readers are security pros. If you’re an employee or a user concerned about personal impact:
- Use a reputable password manager and individual passwords for work and personal accounts.
- Enable multi-factor authentication for email and cloud accounts.
- Use an Email breach checker to check whether your email is compromised, and modify your passwords if you see a match.
The role of continuous improvement
Security is not a project; it’s a program. After handling an Oracle data breach or any other incident, institutionalize learning: update playbooks, refine detection rules, and invest in automation to prevent the same class of event from recurring.
Bulleted summary
- Early detection and strong identity management are the most effective ways to limit damage.
- Combine internal logging with external Dark Web Insights to catch leaks early.
- Containment, evidence preservation, and transparent touch are the three pillars of response.
- Use continuous monitoring and regular exercises to build organizational resilience.
Closing thoughts
An Oracle data breach is more than a technical alarm; it’s a test of people, processes, and governance. The good news is that many of the most effective defenses are practical and affordable: enforce least privilege, centralize and analyze audit logs, and add targeted external monitoring, such as free dark web scanning, as a baseline. By combining these measures with an organized incident response program, organizations significantly reduce the likelihood of a breach and its impact.
FAQs
What immediate step should I take if I suspect an Oracle database was breached?
Contain affected systems and preserve records, revoke compromised credentials, then notify your incident response team for forensic analysis. Early isolation prevents further exfiltration.
Can the dark web tell me if our data was leaked?
Yes, Dark Web Monitoring and deep and dark web monitoring services can reveal listings of stolen data or certifications tied to your domains. Use these findings to guide containment and notification.
Is encryption enough to stop an Oracle data breach from being harmful?
Encryption reduces the value of leaked data but is not a complete defense; attackers who can query translated data or access keys still pose a threat. Combine encryption with access controls and key management.
How often should we run checks to see if employee emails are compromised?
Run automated Check email data breach scans weekly or tie them to onboarding/offboarding events; perform manual reviews after suspicious incidents. Regular checks reduce credential reuse risk.
What is the single best investment to reduce breach risk?
Strengthen identity controls, multi-factor authentication, least privilege, and robust monitoring because most breaches begin with credential misuse. Identity-first defenses offer high impact for cost.